La chine réalise la première communication sécurisée par cryptographie quantique basée sur l’intrication depuis...
Selon une étude publiée le 15 juin dans la revue Nature, des scientifiques chinois ont réalisé la première distribution de clés quantiques au monde...
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
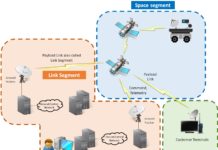
What are the components of a generic Space System
Space Policy Directive-5 (SPD-5), the Nation’s first comprehensive cybersecurity policy for space systems, defines "Space System" as "a combination of systems, to include ground systems,...
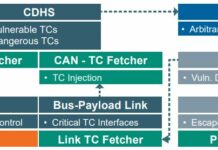
Space Odyssey: An Experimental Software Security Analysis of Satellites
The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper...
Un chercheur alerte sur le risque de piratage des petits satellites comme ceux de...
SpaceX et d'autres sociétés se précipitent pour mettre en orbite des milliers de petits satellites bon marché, mais la pression pour maintenir les coûts...
CYSAT ’21, a space cybersecurity conference : Full Keynotes and Presentations
CYSAT ’21 is the first conference in Europe dedicated to satellite and space industry cyber security. It took place from 17 to 19 March...
Isabelle Tisserand présente le département de cybersécurité satellitaire et spatiale de 3i3s
Isabelle Tisserand est docteur de l’Ecole des Hautes Etudes en Sciences Sociales, anthropologue expert en sécurité et défense. Spécialiste de la protection des patrimoines...
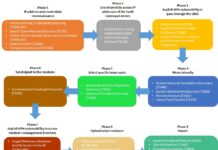
Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Introduction
In this paper, I choose to investigate the Viasat cyber attack that occurred on 24 February, 2022. First, I will summarize the chronology of...
Top 25 most dangerous software weaknesses than can affect satellites in 2023
Issues of vulnerabilities of space systems to cyber attacks has long been ignored for reasons common to industrial systems or SCADA (Supervisory Control And...
CYSAT ’22, a space cybersecurity conference in Paris (April 6-7th 2022)
CYSAT is the first European event entirely dedicated to cybersecurity for space.
After a first successful edition over 2 days in March 2021 with over...