The CNSSI 1253 (Committee on National Security Systems Instruction No. 1253) has released (Attachment 2) the Space Platform Overlay as a companion of the NIST SP 800-53 controsl guide.
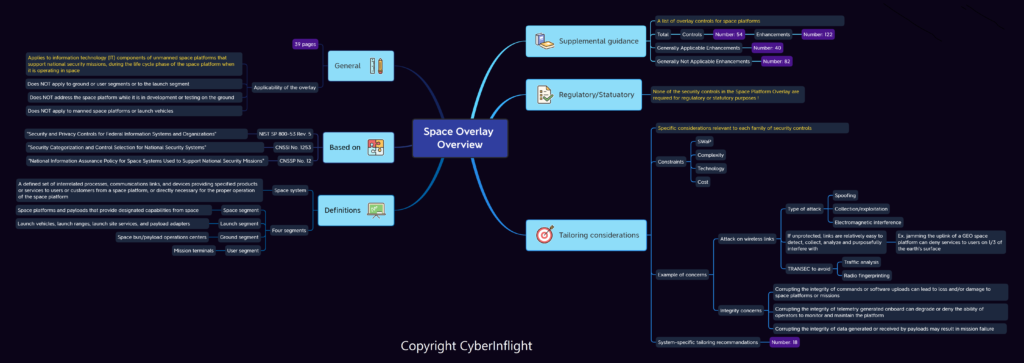
Space Overlay is a set of specific guidances and requirements for space. Space Overlay can be used as Security Baseline on some space systems studies.
But what is a security controls overlay ?
My explanation about an overlay is that an overlay is a customisation of security controls applied to a specific domain, in this case to space domain, which uses the NIST 800-53 controls.
To be more precise : « A specification of security controls, control enhancements, supplemental guidance, and other supporting information employed during the tailoring process, that is intended to complement (and further refine) security control baselines. The overlay specification may be more stringent or less stringent than the original security control baseline specification and can be applied to multiple information systems. »
Thank’s to NIST for this explanation about security controls overlay (more here). Basically, the overlay completes the baseline.
Florent Rizzo from Cyberinflight written an article with a mindmap of the Space Overlay to have a better overview.
Brandon Bailey from Aerospace also written a White Paper (Translating Security Principles for Space Systems to Existing Standards) than mentioned the Space Overlay. The following is an extract from this text (Download Paper – PDF – 15 pages – Oct 1, 2020)
- Government programs and/or organizations have attempted to take portions of NIST governance and apply it to space systems. The most notable attempt at this was with CNSSI 1253 and the generation of the space overlay.
- The space overlay was an attempt to take an existing control set and create an overlay specific for the spacecraft as well as the launch vehicle. Overlays take something that exists (CNSSI 1253 / NIST 800-53) and determine what applies and does not apply.
- The space overlay takes the existing control set and articulates what could be applicable to the spacecraft. The important distinction in this approach is the approach is not risk or threat-informed and is very generic in nature.
- The space overlay has a purpose, but a better approach which aligns with the direction NIST is moving toward in revision 5 of 800-53 is creating a spacecraft baseline.
- The baseline approach starts from a clean sheet of paper and establishes a specific baseline. With this approach, designers/engineers will take the master catalog (i.e., CNSSI 1253 / NIST 800-53 and all the enhancements) and generate their Program/Mission baseline.
- While baseline generation can be labor intensive, it will result in tailored controls/requirements for a particular mission.
- In an effort to promote a threat-informed baseline approach, the engineers need to understand the applicable threats to aid in control derivation.
- To accomplish this, a generic threat library can be used to help identify the threats needing mitigated
The following is an extract ftom the Space Platform Overlay
« This overlay applies to information technology (IT) components of unmanned space platforms that support national security missions, during the life cycle phase of the space platform when it is operating in space (whether experimental1 or operational). This overlay does not apply to ground or user segments or to the launch segment, nor does it address the space platform while it is in development or testing on the ground. The assumptions made in this section about the applicable unmanned space platforms do not necessarily hold true for manned space platforms or the launch, user, or ground segments. »
The main problème with the Space Overlay (which is a great document btw) is that is does not covers the development and testing phases, it only covers pre-op, launch and after launch phases. As mentionned in the document, Space Platform Overlay does not apply to ground or user segments or to the launch segment, nor does it address the space platform while it is in development or testing on. It only apply on unmanned space platforms.
How to address the ground issue ?
We are lucky because Brandon Bailey addressed this issue in the « Re-defining Success of Ground Cyber Assessments » presentation.
From the MITRE Att&CK framework and the right TPPs (Tactics, Technics and Procedures), Brandon Bailey built a specific Ground System TTPs to list some attack paths based on known TTPs used by hackers.
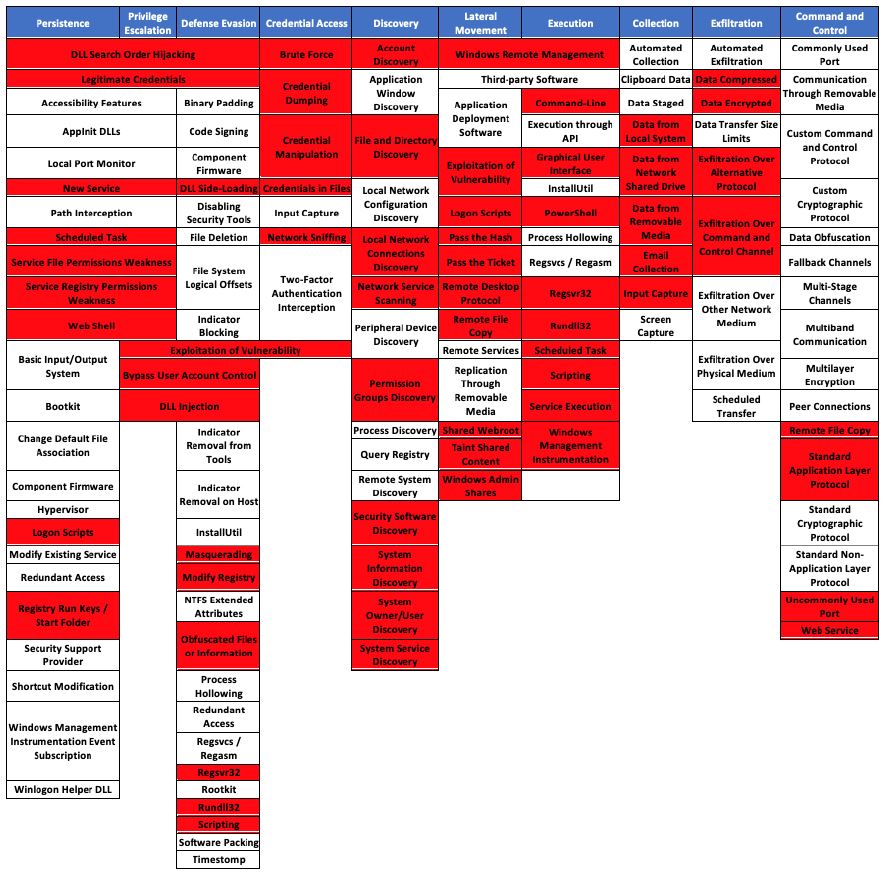
Need to go futhermore ?
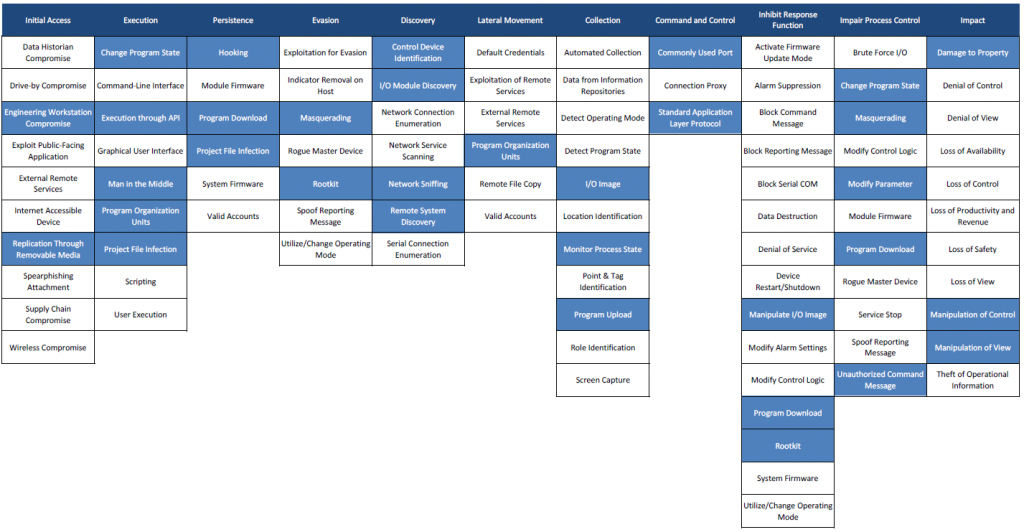
To go futhermore the concept of MITRE ATT&CK framework applied on specific domain, you can also have a look on the MITRE ATT&CK for ICS Matrix.
The MITRE ATT&CK for ICS Matrix is an overview of the tactics and techniques described in the ATT&CK for ICS knowledge base. It visually aligns individual techniques under the tactics in which they can be applied.
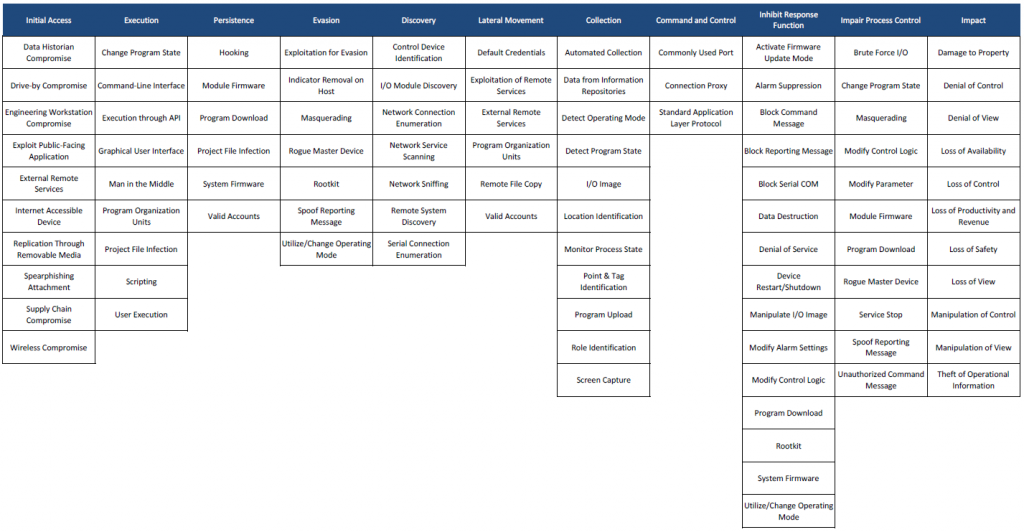
Below is the mapping of Stuxnet attack on the ATT&CK for ICS matrix (Than’ks to Airbus Cybersecurity). « Mapping Stuxnet to the ATT&CK for ICS matrix, as shown in figure 3, quickly shows how complex this attack was. Business risk owners can now identify which techniques to focus on if they need to minimise the risk from strikes like Stuxnet. »