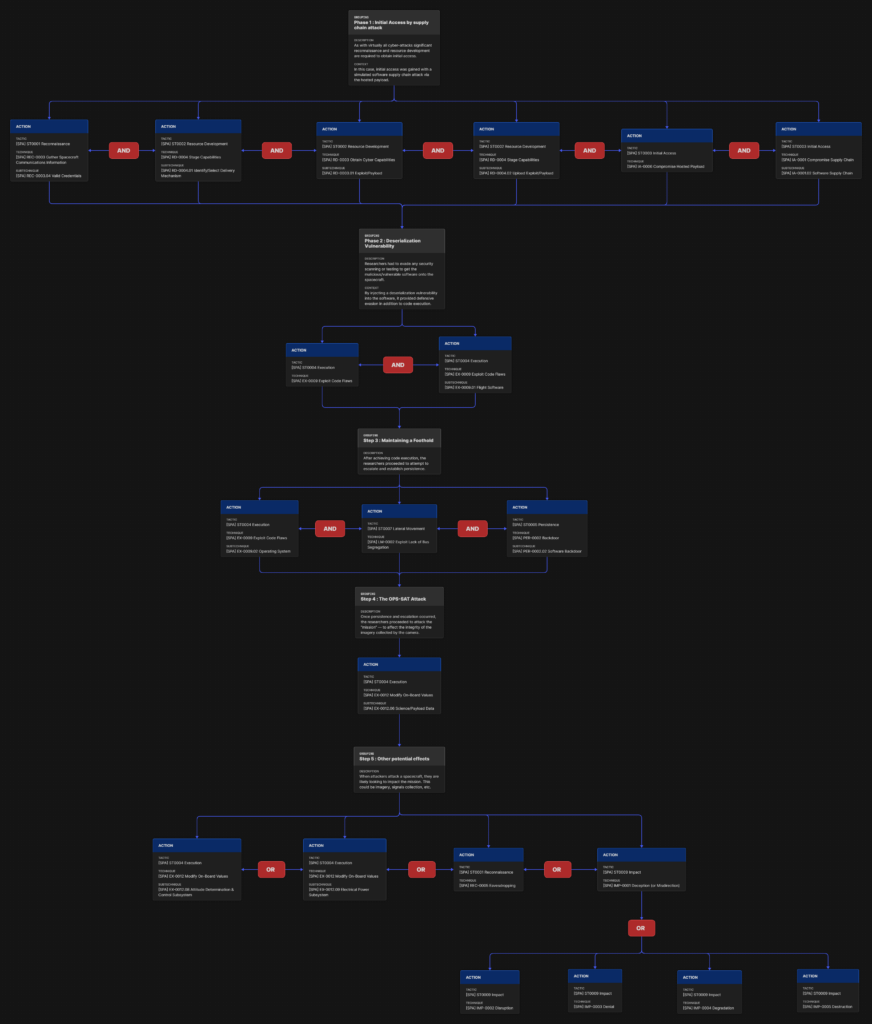
In 2023, during the CYSAT conference, Thales presented a live demonstration of a satellite hacking scenario, a milestone event that shed light on the cybersecurity challenges of modern space systems. Since then, various experts have analyzed this simulation to better understand how cyberattacks could target satellite architectures and mission operations.
Context and Background
As part of this effort, Brandon Bailey and Brad Roeher from the SPARTA team conducted a detailed analysis of the Thales demonstration using the SPARTA (Space Attack Research and Tactic Analysis) Framework. Their work, which I describe in this article, identified the key Tactics, Techniques, and Procedures (TTPs) involved across the attack lifecycle, creating a foundation for understanding adversarial behavior in space environments.
In parallel, Kevin Jahaziel Leon Morales and Romel Marin from the PWNSAT team extended the MITRE ATT&CK Flow Builder tool to natively integrate the SPARTA framework. This enhancement allows researchers to automatically generate and visualize space-specific attack flows, a breakthrough for modeling realistic cyberattack scenarios targeting satellites and related ground segments.
My Objective and Methodology
Building on these complementary works, I set out to reconstruct the entire attack flow of the Thales satellite hacking demo using this upgraded ATT&CK Flow Builder. My goal was to combine the analytical rigor of SPARTA TTPs identified by the SPARTA team with the visual modeling capabilities of the MITRE ATT&CK Flow Builder modified by the PWNSAT team.
I already conducted a such work by modeling Viasat Cyber Attack but with the real MITRE Attack Flow Builder. You can check this work in this article in which I also explain what is the Attack Flow Builder Tool designed by MITRE Engenuity’s Center for Threat-Informed Defense (CTID).
How I achieved this work
The methodology described below is showing the building process that I used to achieve this work :
- I collected the TTPs identified by the SPARTA team (Bailey and Roeher) during their analysis of the Thales demonstration.
- I used the pwnsat-modified ATT&CK Flow Builder, which supports direct integration with SPARTA taxonomy.
- I constructed a visual diagram mapping the complete sequence of attacker actions, from initial access through payload manipulation to mission impact.
- I validated the consistency of each mapped step with the SPARTA methodology to maintain analytical accuracy.
The resulting diagram captures not only the technical flow of the attack but also the relationships between threat actions, affected assets, and tactical objectives.
Result of my work
The diagram below is showing the result of my work. Original file in big format can be found below.
Text inside the grouping action box are from SPARTA.
The format used for creating and editing in the Attack Flow Builder is the AFB builder format (.afb). The AFB file below can be used to open the project for further editing in the future.
The PNG format is used to save the flow. This format is great for visualizing, using in presentations, sharing with others, etc..
Why This Work Matters
This experiment serves multiple purposes:
- Educational value: It helps practitioners and researchers visualize how real-world satellite attacks unfold, bridging the gap between theoretical TTPs and operational behaviors.
- Framework interoperability: It demonstrates how SPARTA and MITRE ATT&CK can coexist and complement each other in cyber threat modeling.
- Scenario replication: The approach can be reused to analyze other aerospace or defense-related use cases, accelerating structured threat simulation and red-team exercise design.
- Community advancement: By using open frameworks and shared methodologies, this work contributes to a growing ecosystem of collaborative research in space cybersecurity.
For further details
- Explore the official SPARTA updates here : https://medium.com/the-aerospace-corporation/sparta-v3-1-whats-new-58d6b91b1505
- Explore related research on unified attack flows in the space and embedded domains here : https://pwnsat.org/blog/from-mitre-attck-to-sparta-a-unified-attack-flow-for-space-systems/
- If you want to test this fork check the repo here and check the UI here.
Next Steps
By sharing both the diagram and the building process with the research community, my goal is to encourage others to apply the same methodology to new studies. Whether you’re an academic researcher, a red teamer, or part of a mission assurance team, these tools can help you better model and mitigate cyber risks in space systems.