In this article, we will try to identify the various threats to space systems.
This article is a synthesis of the CSIS (Center for Strategic and International Studies) report on the Space Threat Assessment 2020. The slides used to illustrate the article are from a presentation by Todd Harrison, the Director of Defense Budget Analysis and Aerospace Security Project at CSIS.
The first satellite in space was the Russian Sputnik satellite launched in 1957. Immediately after this feat, the United States began the first studies for the development of anti-satellite weapons called ASAT (for Anti-Satellite). The first interception test of a satellite was carried out by the Americans on 13 October 1959. It was a Boulder Ryan missile launched from a bomber whose objective was to detonate a nuclear bomb close to the satellite in order to destroy it.
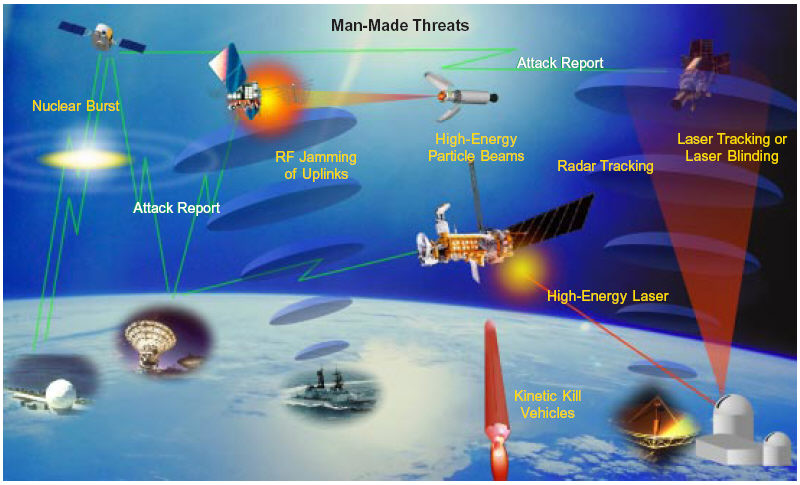
This type of anti-satellite weapon (ASAT) is called a kinetic weapon. But there are many others. Let’s explore together the landscape of threats to satellites.
What has changed in space?
What has changed in space to create new threats? There are what we call the 4Ds: Diverse, Disruptive, Disordered and Dangerous.

Space is more Diverse
Until the 1990s, space was mainly dominated by the two great powers USA/USSR whose Cold War confrontation was coming to an end. Until then, these were mainly military satellites. The Russians also had a problem with the longevity of their satellites, so they had to launch them more often. That’s why they became so good at launching them.
From the 1990s onwards, the US/USSR duopoly began to diminish, leaving more room for diversity in the space landscape with greater development of the Europeans but also of China.
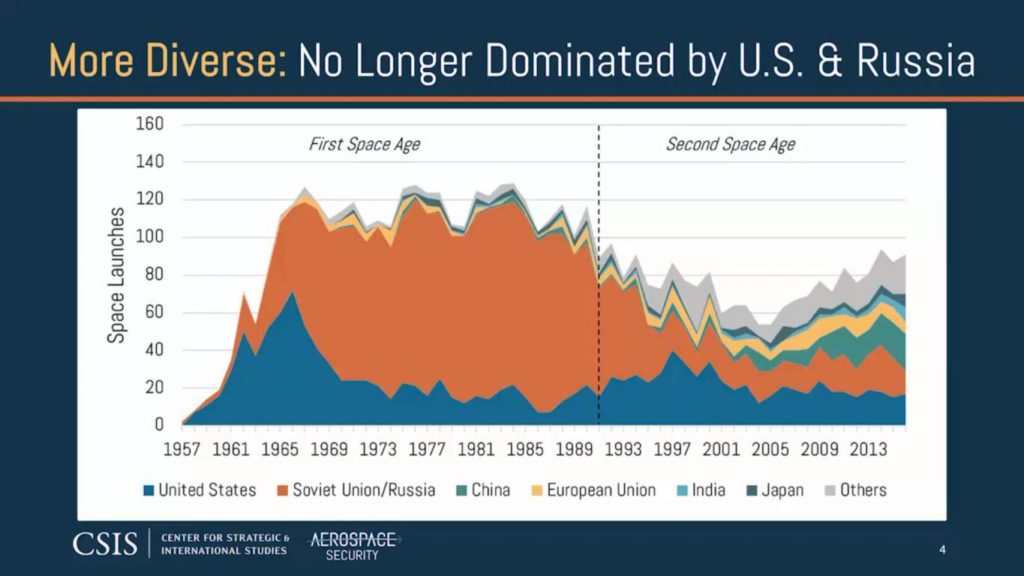
Space is more Disruptive
With the diversity of the space landscape also comes the diversity in the use of satellites, moving from predominantly military use to increasingly commercial use.
Satellite imagery is developing more and more. Meteorological satellites are also arriving, as well as communications satellites. It is the SpaceX company that will bring disruption to the space sector with the ability to bring back launchers that land on earth.

Space is more Disordered
Inevitably, with increasingly diverse and disruptive uses, space societies have practices that do not always comply with laws and treaties.
In order to launch and operate satellites, licences must be obtained from the International Telecommunication Union (ITU) and the Federal Communications Commission (FCC). The first Cubesat satellites, such as the SpaceBee 1-4, which are small satellites with a side length of 10 cm, were refused licenses.
Similarly, to be able to take satellite pictures of the Earth, a license from the NOAA (National Oceanic and Atmospheric Administration) is required. Obviously, SpaceX has not understood this because it systematically carries small cameras to film its in-flight operations and the Earth is systematically seen in the background.
Similarly, when Elon Musk conducted the test of the Falcon Heavy Rocket, he took the opportunity to put one of his red Tesla into orbit. And so that everyone could see the car, he put small cameras all around it that film and photograph the Earth.
All the satellites now have cameras. You can see that laws and treaties are not designed for today’s uses.

Space is more Dangerous
More and more activity depends on space. Military missiles are now guided by satellite. On the slide you see a U.S. drone, the General Atomics MQ-9 Reaper, which is guided not only by radio but also by a satellite link called SATCOM. The ships get their position from GPS. During combat maneuvers, communications and positioning can be done in real time via satellite.

All these uses show that we have become increasingly dependent on space while most of these uses are not adequately protected in the face of an ever-increasing proliferation of threats.
In 2007, the Chinese acknowledged that they had carried out an ASAT (anti-satellite) test by destroying one of their own meteorological satellites, creating thousands of pieces of debris threatening other spacecraft. We are talking about more than 3,000 large pieces of debris and several thousand small pieces of debris. More recently, in 2015, the Chinese acknowledged that they have conducted further ASAT tests using DN-3 missiles.
On the other hand, an ASAT shot is unambiguously a hostile act towards a nation. One is able to know who did it, to detect the origin of the shot, many observers can witness it. All this has a deterrent effect, so that there are practically no ASAT tests.
On the other hand, the most feared threats are those with the most difficult attributions. We are talking about jamming systems. These are invisible attacks, where nothing explodes, no one dies, and no one is aware of them. Unlike ASAT attacks, which are irreversible, jamming attacks are reversible. They can be activated and deactivated at will. This type of threat is really very insidious to deal with.
In the slide in the top right-hand corner, you can see, for example, GPS jammers and SATCOM (satellite communications) jammers that are mounted on trucks. Russia has developed a lot of them and they’ve used them in Ukraine and Syria.
On the left side, we can see another threat to space systems that is very difficult to deal with. These are laser precision weapons that are used to dazzle or blind imaging satellites. It is also another type of attack that is very difficult to deal with.

All the examples we have just reviewed show that we have more and more uses that depend on space. And in parallel with this dependence, we realize that space systems are increasingly exposed to threats and vulnerable to attack.
What are the different threats to space systems?
There are four main families of threats to space systems:
- Kinetic physical threats
- Non-kinetic physical threats
- Electronic Threats
- Cyber threats
Kinetic physical threats

Physical kinetic threats are weapons that attempt to strike directly or detonate a warhead in the vicinity of a satellite or ground station. This can be done either by an ascending trajectory ASAT or by an ASAT that crosses the orbit of the target satellite.
A co-orbital ASAT differs from a direct ascent ASAT in that a co-orbital ASAT must first be placed in orbit and then manoeuvred to reach its target. TSOAs can remain dormant in orbit for days or even years before being activated. The guidance system on board such ASATs requires a relatively high level of sophistication and technology as well as significant testing and deployment resources.
Ground stations are more vulnerable than orbiting satellites. They are threatened by more traditional weapons such as military weapons, guided missiles and long-range missiles. Ground stations can also be disrupted indirectly by attacks on the power grid or communications.
Kinetic physical attacks usually have irreversible effects on their targets. They can be attributed more or less easily by identifying the source of the attack. If the attack is successful, its effect is likely to be publicly visible either through orbital debris or through the damaged ground station. All this provides a deterrent to this type of attack.
Non-kinetic physical threats

Non-kinetic physical threats represent weapons such as lasers, HPM (high-powered microwave) weapons and EMP (electromagnetic pulse) weapons. These are weapons that have physical effects on their target but do not establish physical contact. These attacks often take place at the speed of light. In most cases, they are invisible and therefore very difficult to attribute.
High-powered lasers can be used to damage or degrade sensitive satellite components such as solar panels. Lasers can
can also be used to temporarily or permanently dazzle sensitive satellite sensors. Targeting a satellite from the Earth with a laser is no small task since the laser passes through the atmospheric layer. This requires a very good quality beam and advanced pointing control, not to mention the sophistication and cost of the technology.
The difficulty for the attacker is that he has a very limited ability to know whether his attack was successful or not.
An HPM-type weapon can be used to disrupt the electronics of a satellite, corrupt the data stored in memory, cause processors to restart, or, at higher power levels, cause irreversible damage to electronic circuits and processors.
Electromagnetic waves, on the other hand, disperse and weaken with distance and the passage through the atmosphere. This is why it is preferable to carry out an HPM-type attack from another satellite in orbit.
Electronic threats

Electronic threats are attacks by jamming or usurpation of radio frequency (RF) signals. Jamming is a form of electronic attack that interferes with RF communications by generating noise in the same frequency and field of view as the antenna of the targeted satellite or receiver.
Interference can interfere with either uplinks from the ground to the satellite such as Command and Control communications, or downlinks from the satellite to the ground such as to users (see our article on the components of a satellite C&C system). Jammers can target satellite dishes, GPS receivers, satellite phones.
The technology needed to jam signals is commercially available and relatively inexpensive. Jamming is a reversible form of attack in that, once the jammer is turned off, communications return to normal. Jamming is also an attack that can be difficult to detect or distinguish from accidental interference.
RF signal spoofing is a form of electronic attack in which the attacker traps a receiver by sending a false signal produced by the attacker. Satellite downlink spoofing is a form of electronic attack in which the attacker traps a receiver by sending a false signal produced by the attacker.
can be used to inject false or corrupted data
If an attacker succeeds in usurping the Command and Control signal from an uplink to a satellite, it could take control of the satellite for malicious purposes.
A form of RF signal spoofing attack called “meaconing” allows military GPS signals to be spoofed even if they are encrypted. Meaconing does not require breaking the GPS encryption. It simply rebroadcasts a copy of the signal that is out of time or with altered data.
Cyber threats

Unlike electronic attacks that interfere with the transmission of RF signals, cyber attacks target the data itself as well as the systems that use that data. Satellite antennas, antennas of ground stations, communication lines that connect the stations to the terrestrial networks, user terminals that connect to the satellite, are all potential targets for attack and may be subject to intrusion attempts.
Cyber attacks can be used to determine who communicates with whom, to eavesdrop on traffic or to inject corrupted data and malformed packets into systems.
Cyber attacks require a high level of knowledge and understanding of the environment. However, they do not necessarily require very significant resources.
Cyber attacks can be contracted to private groups or individuals, which means that a state or non-state actor lacking internal cyber capabilities can still be a cyber threat.
A cyber attack on a space system can result in loss of data, disruption or even the permanent loss of a satellite. For example, if an adversary manages to take control of a satellite’s Command and Control system, the attacker could cut off all communications, increase its propulsion power, damage its electronic equipment and its sensors and ultimately irreversibly damage the satellite.
Accurately attributing a cyber attack can be difficult, if not impossible. Attackers typically use a variety of methods to conceal their identity,
such as the use of hijacked servers.
Summary of threats to space systems
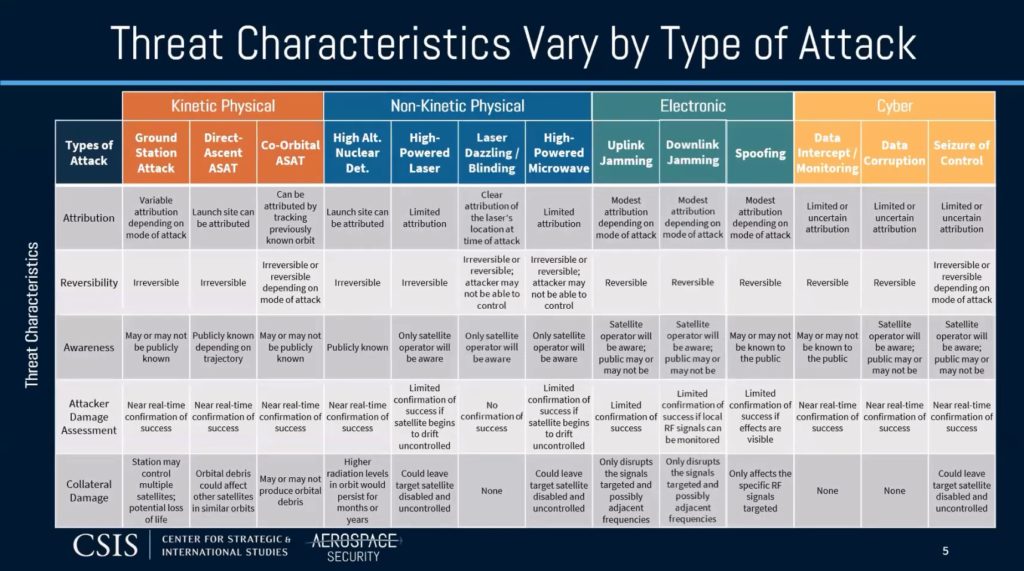
The two CSIS tables below are a synthesis of threats to space systems. The first summarizes the 4 main threat families with their characteristics.

The CSIS table below provides a summary of all the threats we have just looked at and shows that their characteristics vary depending on the type of attack.
Our next article will be dedicated to Cyber threats to space systems.
Resources
The full Space Threat Assessment 2020 report has been available since April 2020 on the CSIS website.
On the same theme, the Secure World Foundation (SWF) has also published an assessment report on the harmful capacity in space. The report is available on the SWF website.