Kaspersky Lab experts were the first to reveal in 2015 that the Russian hacker group Turla APT had exploited and hijacked satellite feeds to hide their Command & Control (C&C) servers.
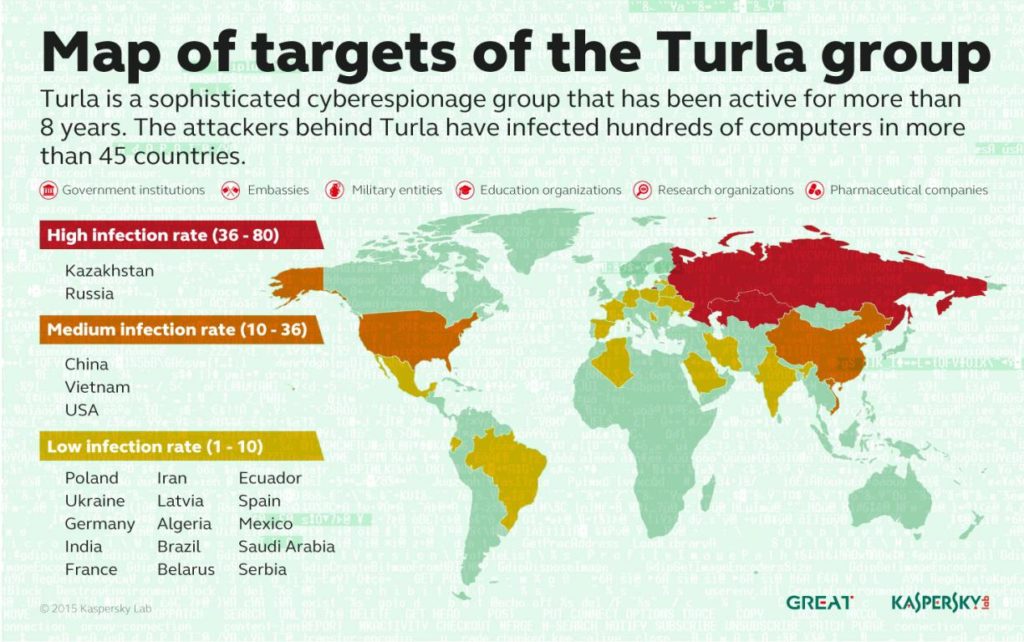
As a reminder, the Turla APT group, also known as Snake or Uroburos, had in 2015 affected more than 500 victims in 45 different countries around the world, including government agencies, military entities and diplomats as the group’s preferred targets.
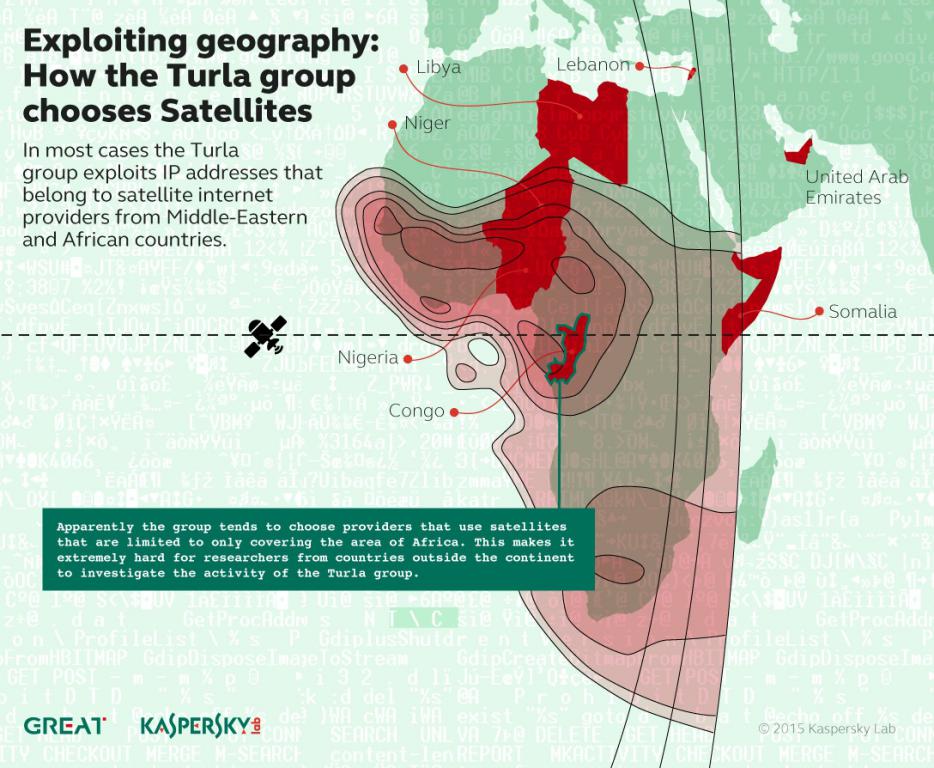
While satellites are best known as tools for broadcasting and secure communication, they are also used for Internet access. Their services are mainly used in remote locations where all other means of Internet access are either unstable and slow or totally inoperative.
One of the most widespread and inexpensive methods of satellite Internet access is an exclusively downlink, with the uplink being via conventional low-speed Internet access.
The use of a satellite internet connection offers undeniable advantages such as anonymity. Indeed, apart from knowing that you are under satellite coverage, it is very difficult if not impossible to physically know your location.
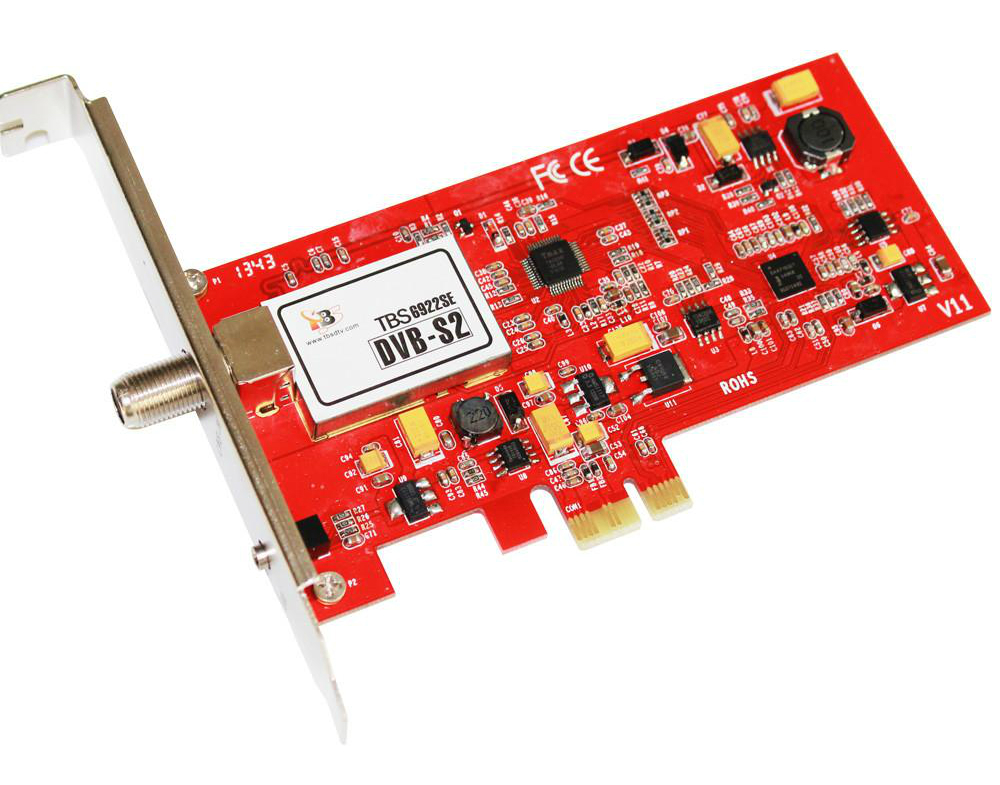
Another advantage of hijacking satellite links is the low cost of hardware investment. Here, hackers have hijacked a DVB-S satellite link. To hijack this type of link, you need the following items, the cost of which is estimated at less than 1000 euros:
- A satellite dish, the size of which depends on the geographical position and the satellite.
- A universal head
- A dedicated DVB-S tuner (PCIe card)
- A computer, preferably running Linux
PCIe TBS-6922SE card for DVB-S canal receptionThe method is not new. It goes back to the 2010’s with the Skygrabber software. A person with a PC and a satellite dish can, with the software, intercept downloads requested by Internet users connected to a satellite. Indeed, the downlink transmitted from the satellite in geostationary orbit to the computer was not encrypted at the time.
How a satellite internet connection is hijacked
The SecureList.com site explains the technique very well. The Turla APT group has exploited a weakness of satellite internet connections of the DVB-S type which is that the stream is not encrypted.
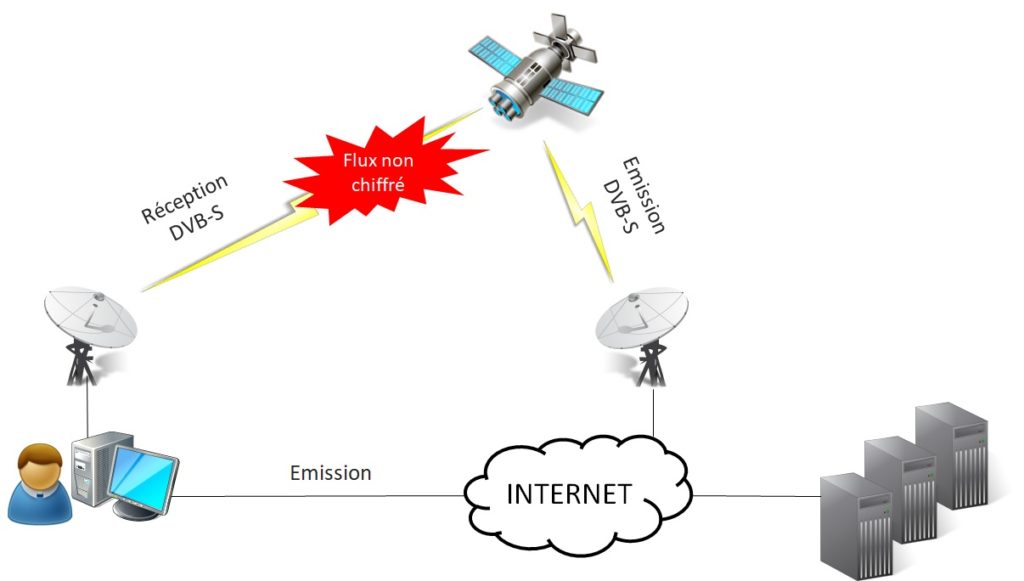
The technique used here is not Man-In-The-Middle but IP Spoofing.
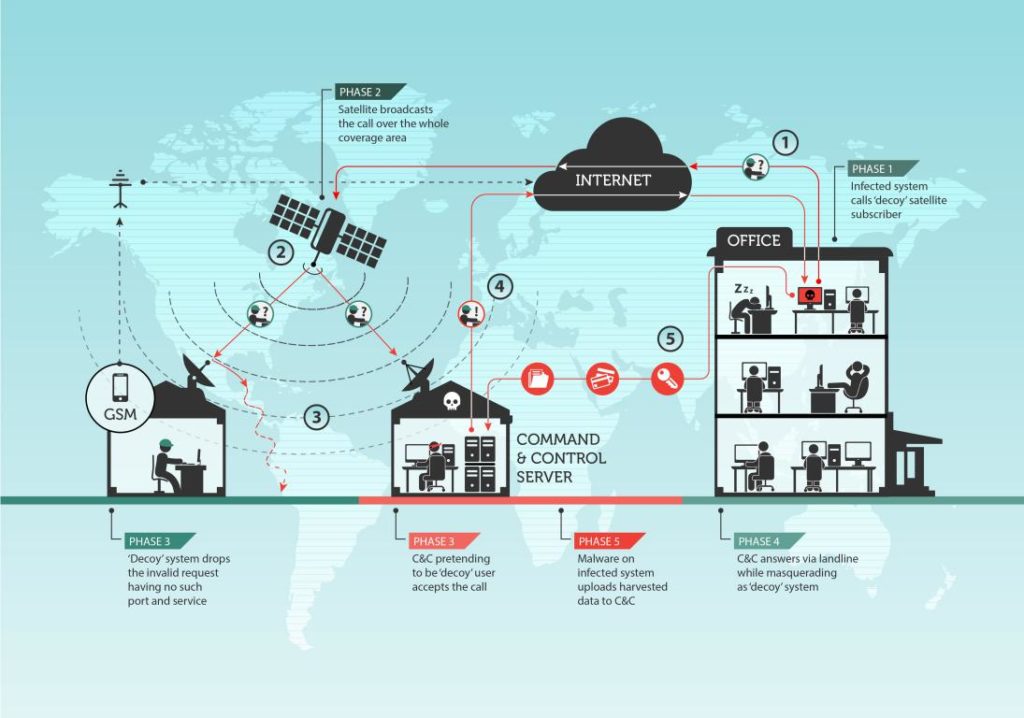
- The group starts by “listening” to the satellite downlink in order to identify the active IP addresses of the Internet users connected to the satellite.
- It chooses a connected IP address to use it to mask a C&C server, without the knowledge of the legitimate user. To do this, he configures the domain name of his Command & Control server to use one of the active IP addresses connected via satellite.
- Machines infected with the Turla malware are instructed to filter data to the domain name whose IP addresses correspond to Internet users connected via satellite (hackers use so-called dynamic DNS hosting, which allows them to change the IP address of a domain at will).
- The malware on the infected computers then contacts the IP address of the legitimate user connected to the satellite to establish a TCP/IP connection.
- The data is routed via conventional lines to the teleports of the satellite Internet service provider, then to the satellite, and finally from the satellite to the user whose IP address has been chosen.
- This user’s machine will abandon the connection because the communication is not intended for him (the port chosen by the attackers is not open on the user’s machine).
- The same TCP/IP connection request is also sent to the attackers’ Command & Control server, which uses the same IP address and will respond to the infected machine to establish a communication channel and receive the exfiltered data.
Interestingly, as you will have noticed, the legitimate user, whose IP address has been used by hackers to retrieve data from an infected machine, also receives these data packets but hardly notices them. In fact, Turla members instruct infected machines to send data to ports that, in the majority of cases, are closed by default. As a result, the legitimate user’s computer simply discards these packets, while the Turla C&C server, which keeps these ports open, receives and processes the exfiltered data.
The legitimate satellite user will not even notice that his satellite connection has been hijacked unless he checks his event logs and notices packets being discarded by his satellite modem. But this will look more like “Internet noise” than suspicious traffic.
Short explanatory video
The use of satellite links to hide a Command & Control server and control a botnet is not exclusive to Turla APT. Researchers have observed that other APT groups also rely on satellites to manage their malware such as Rocket Kitten or Xumuxu or the Hacking Team in Italy. We’ll talk about this in a future article.
The question now is whether DVB-S satellite internet connections are now encrypted to protect confidentiality and integrity. If anyone has the answer, I’d like to have it as a comment. This will also be the subject of a future article.
Source and technical details on Kaspersky Lab’s SecureList.com website.