CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading European cybersecurity and space exhibition that took place 26th-27th April in Paris (Station F). This is the biggest European event entirely focused on cybersecurity for the space industry.
Since 2021, the event brings space and cybersecurity experts together to create a European ecosystem capable of responding to the current and future challenges faced by the European space industry.
Faced with cybersecurity challenges and the growing importance of data protection in space, it is crucial to bring together communities of cybersecurity experts to build a European ecosystem capable of addressing current and future industry challenges.
Last years’ event saw more than 450 space specialists, decision-makers and experts come together. In its third year, CYSAT highlighted Europe’s cybersecurity capabilities and solutions dedicated to space from both a technological and geostrategic perspective.
To find the full programme and more information on the event, visit: https://cysat.eu/
Mathieu Bailly, VP at CYSEC, Co-founder and Director of CYSAT, has published on his linkedin profile what was the point of the Thales demo at CYSAT. First, Mathieu what was NOT part of the demo.
We publish these key takeaways below with his permission. Thank’s to Mathieu for sharing whith us its key takeaways.

Thales demo at CYSAT: what was the point again??
First, what was NOT part of the demo ❌
1️⃣ The ground segment ❌
For the short-medium term it is reasonable to assume that cyber attacks on space systems disturbing the nominal operations of the mission (i.e. taking control of the spacecraft bus and/or payload but excluding eavesdropping) remain ground-based.
That means discarding scenarios involving rogue satellites with capabilities to perform non-cooperative rendez-vous. To me that’s fair for the next 5 years.
2 main scenarios:
1. the spacecraft is flying and operational
👉 then the attacker has to go through the ground segment (mission control, ground stations, etc) before reaching the spacecraft
👉 the attacker is capable to send TMTC that are valid and executed on board without the operator noticing or able to react (e..g via its own ground stations)
2. the spacecraft is under development on ground (design, assembly, test, transport, launch)
👉 the attacker manages to access information (e.g. cryptographic keys) or to install a malware / backdoor on board (e.g. corrupting the flight control software)
These are the typical scenarios with the biggest likelihood x severity scores.
👉 None of the above were covered by the Thales demo since the ground segment was out of the scope as the team was granted the access to OPS-SAT (as any other experimenter).
2️⃣ On-board: not representative of most missions ❌
🔹On-board, OPS-SAT is also very « unique » since it’s been pioneering many technology innovation like flying Linux, re-configuring FPGAs on a daily basis, etc (read all OPS-SAT firsts here 🔗 https://lnkd.in/eC3eDgDv) 💪
👉 So the demo by Thales has been done a spacecraft that is currently not representative of the current missions in operations or close to the launch pad (especially institutional missions!)
❓ So what was the point of this demo then ❓
I’m getting there!
🔹The point was to show that current space tech trends (advanced on-board processing, regular in-orbit reconfiguration, as a service models, etc) are all great progress that will soon be adopted by most operators BUT that come at the expense of greater cyber risks 👾
🔹And currently the space industry (especially #newspace) is embracing these innovations without the security culture that should come with it 🤠
👉That’s why showing how security experts can manipulate data, take control of the Attitude and Control system of a modern spacecraft by using various methods of privilege escalation exploiting flaws on access management and Linux helps to spread the word: 📢 BE PREPARED!
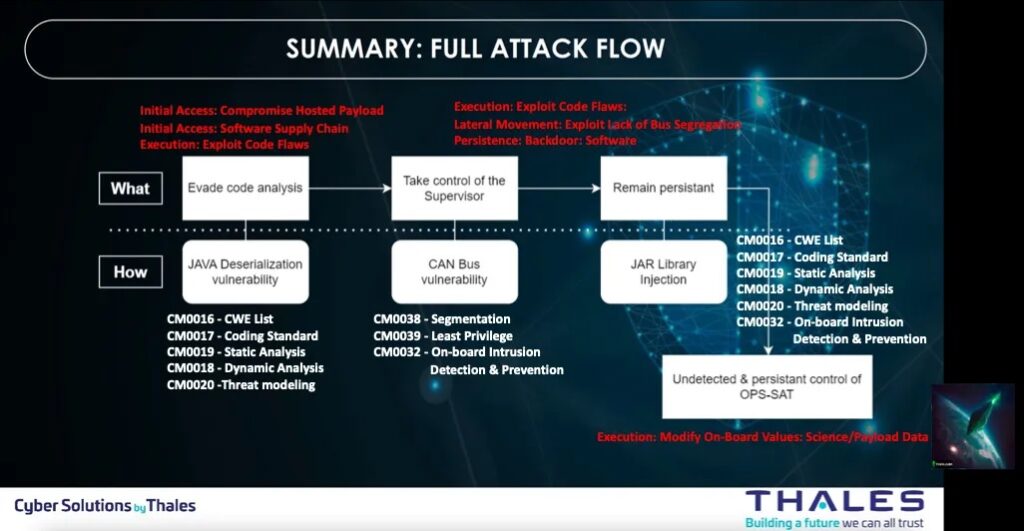
Summary of the full attack flow
Check this demo in video
An analysis of the CYSAT 2023 Demo by SPARTA team
Brandon Bailey & Brad Roeher from the SPARTA team analyzed, in this article, Thales Group’s CYSAT ’23 presentation material to deconstruct the experiment, extract lessons learned, and document potential countermeasures.
The SPARTA (Space Attack Research and Tactic Analysis) Framework was used to identify the tactics, techniques, and associated countermeasures associated with the experiment/attack.
They utilized the SPARTA Navigator tool to construct the attack chain and generated an Excel export to pinpoint relevant countermeasures. Subsequently, a thorough analysis is conducted to ensure the applicability of the associated countermeasures to the specific Tactics, Techniques, and Procedures (TTPs).
The SPARTA Navigator proves invaluable in presenting a comprehensive array of countermeasures categorized by defense-in-depth, effectively minimizing the risk posed by TTPs. By leveraging the SPARTA Navigator, we successfully map the attack chain to SPARTA TTPs, as exemplified below.
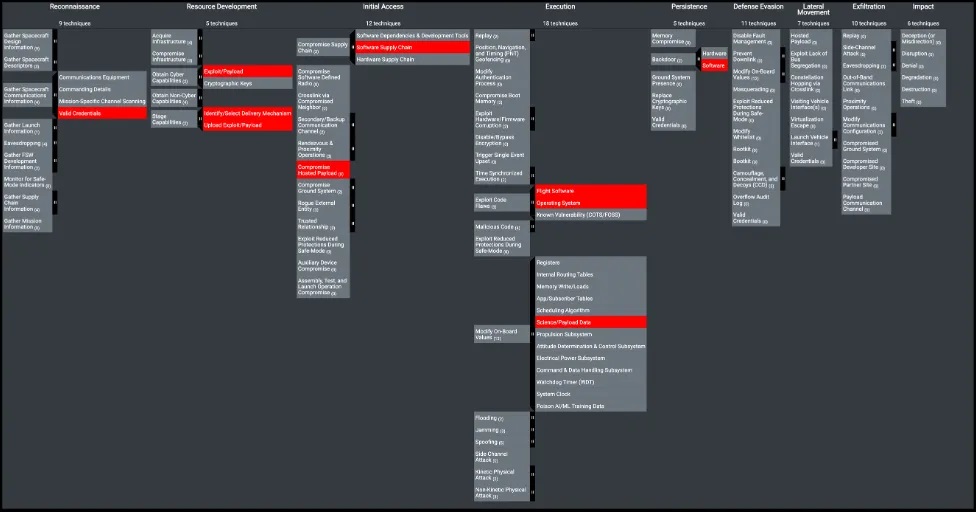
Upon exporting the data from the SPARTA Navigator, they have identified eight countermeasures. Out of these, five pertain to terrestrial countermeasures intended to prevent vulnerable software from infiltrating the spacecraft. The remaining three countermeasures are implemented onboard the spacecraft itself, serving to protect against and/or detect the TTPs executed during the experiment.
All 2023 CYSAT videos are online
All videos about 2023 CYSAT in Paris, the biggest European event around cybersecurity for commercial space, are online and can be seen here.
A propos de CYSEC
CYSEC is a Franco-Swiss cybersecurity company that is a pioneer in the protection of satellites and data collected and transmitted in space.
The company has just launched two security products in 2023, ARCA SATCOM dedicated to the satellite internet market, and ARCA SATLINK dedicated to constellation operators.
For more information : www.cysec.com