Espaces extra-atmosphériques et cyberespace : éléments d’approches croisées
Le cyberespace et les espaces extra-atmosphériques sont les deux « nouveaux » milieux de conflictualité du 21ème siècle. Leur nouveauté tient moins à leur création (le...
La chine réalise la première communication sécurisée par cryptographie quantique basée sur l’intrication depuis...
Selon une étude publiée le 15 juin dans la revue Nature, des scientifiques chinois ont réalisé la première distribution de clés quantiques au monde...
Isabelle Tisserand présente le département de cybersécurité satellitaire et spatiale de 3i3s
Isabelle Tisserand est docteur de l’Ecole des Hautes Etudes en Sciences Sociales, anthropologue expert en sécurité et défense. Spécialiste de la protection des patrimoines...
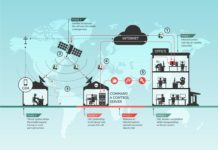
Un chercheur alerte sur le risque de piratage des petits satellites comme ceux de...
SpaceX et d'autres sociétés se précipitent pour mettre en orbite des milliers de petits satellites bon marché, mais la pression pour maintenir les coûts...
Qu’est-ce que le grand Commandement De l’Espace (CDE) créé par la France pour la...
Le Commandement De l’Espace (CDE) a été créé par arrêté le 3 septembre 2019. Il succède au Commandement interarmées de l’espace (CIE). Il rassemble...
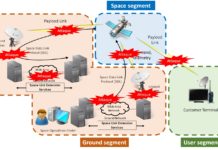
Etude sur la cybersécurité des systèmes spatiaux : menaces, vulnérabilités et risques
A la différence des attaques électroniques qui interférent avec la transmission des signaux de Radio Fréquence, les cyberattaques visent quant à elles, les données...
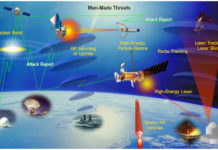
What are the threats to space systems?
In this article, we will try to identify the various threats to space systems.
This article is a synthesis of the CSIS (Center for Strategic...
Back to Turla or how a Russian-speaking cyber-espionage group exploits satellites
Kaspersky Lab experts were the first to reveal in 2015 that the Russian hacker group Turla APT had exploited and hijacked satellite feeds to...
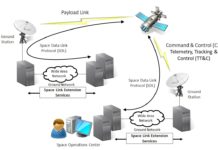
Description of the Elements of a Satellite Command and Control System
In order to be able to analyse the various threats and identify the risks facing a space system, it is necessary to describe precisely...
First CTF in space with Hack-A-Sat: the US Air Force launches a Bug Bounty...
It was the TechCrunch site that revealed the information. The U.S. Air Force will launch a bug bounty program in the form of a...