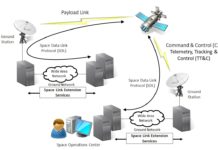
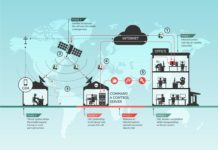
Description of the Elements of a Satellite Command and Control System
In order to be able to analyse the various threats and identify the risks facing a space system, it is necessary to describe precisely...
An analysis of the Viasat cyber attack with the MITRE ATT&CK® framework
Disclaimer
To do this analysis of the Viasat cyber attack, I used the open-source intelligence (1) of the team composed by Nicolò Boschetti (Cornell University),...
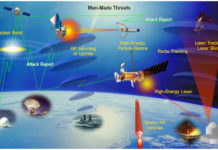
What are the threats to space systems?
In this article, we will try to identify the various threats to space systems.
This article is a synthesis of the CSIS (Center for Strategic...
Qu’est-ce que le grand Commandement De l’Espace (CDE) créé par la France pour la...
Le Commandement De l’Espace (CDE) a été créé par arrêté le 3 septembre 2019. Il succède au Commandement interarmées de l’espace (CIE). Il rassemble...
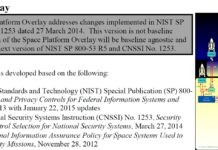
CNSSI 1253 and NIST released the Space Platform Overlay
The CNSSI 1253 (Committee on National Security Systems Instruction No. 1253) has released (Attachment 2) the Space Platform Overlay as a companion of the...
Cartographie des acteurs français et européens de la cybersécurité satellitaire et spatiale
La France est leader de la politique spatiale en Europe. Elle met en oeuvre des projets innovants et performants avec en permanence de nouveaux...
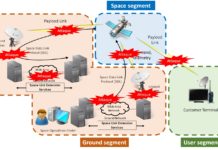
Etude sur la cybersécurité des systèmes spatiaux : menaces, vulnérabilités et risques
A la différence des attaques électroniques qui interférent avec la transmission des signaux de Radio Fréquence, les cyberattaques visent quant à elles, les données...
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
Back to Turla or how a Russian-speaking cyber-espionage group exploits satellites
Kaspersky Lab experts were the first to reveal in 2015 that the Russian hacker group Turla APT had exploited and hijacked satellite feeds to...
New upcoming course : “Aerospace Cybersecurity: Satellite Hacking” made by Angelina Tsuboi in collaboration...
We are very excited to announce a new upcoming course, "Aerospace Cybersecurity: Satellite Hacking" led by Angelina Tsuboi in collaboration with PenTestMag.
This comprehensive course...