Ce soir, mercredi 27 mai 2020, l’histoire va se dérouler sous vos yeux. La NASA et SpaceX lancent les astronautes Robert Behnken et Douglas Hurley vers la Station spatiale internationale. Cette mission marque le retour, depuis le retrait de la navette spatiale en 2011, des américains dans les vols habités vers la station spatiale depuis le sol américain.
Soyez à l’écoute des différentes chaînes Youtube qui vont couvrir et commenter l’événement comme celle bien sûr de la NASA mais aussi des chaînes Youtube françaises comme celles d’Hugo Lisoir et “Cosmogonia Live“.
A partir de 18h15 CEST, la NASA et SpaceX assureront une couverture conjointe et en direct du lancement de la capsule Crew Dragon jusqu’à l’arrivée à la station spatiale. Les équipes visent 22h33 CEST pour le lancement du vaisseau spatial SpaceX Crew Dragon au sommet d’une fusée Falcon 9 depuis le complexe de lancement historique 39A au Centre spatial Kennedy de la NASA en Floride. Le Crew Dragon devrait s’amarrer à la station spatiale, le lendemain vers 17h29 CEST, le jeudi 28 mai.
Toutes les images pour se mettre dans l’ambiance du vol
Pour rappel, il s’agit du premier lancement d’une fusée américain avec un équipage depuis 2011. Un moment crucial à ne pas rater pour le programme spatial américain.
Stardust
La chaîne YouTube Stardust sera en direct avec Hugo Lisoir qui sera accompagné de Marie-Ange Sanguy, la rédactrice en chef d’Espace & Exploration et de Julia Bergeron, du site anglophone NASA Spaceflight.
Hugo Lisoir
Hugo Lisoir sera aussi en direct sur Twitch. Voici son message : Hello ! Donc demain si tout va bien on sera en live vers 19h/20H pour suivre ce vol !ATTENTION pour l’instant la météo n’est pas parfaite (go météo à 60%)
Le lien -> https://www.twitch.tv/hugolisoir
NASA TV LIVE
Cosmogonia Live
La chaîne Youtube “Cosmogonia Live” propose de suivre en LIVE l’événement
FALCON 9 | DEMO 2 – Lancement (français)
Live de SpaceX
Everyday astronaut
What About It
NBC News
Clubic
Sur Twitch avec Arthur et Eric Bottlaender. Les invités sont Jean-François Clervoy et Xavier Pasco
Space Explorer W
Sur Twitch avec comme invités Isabelle (Idariane / Rêves d’Espace) et Olivier Sanguy (Cité de l’Espace)
Vidéo explicative du vol
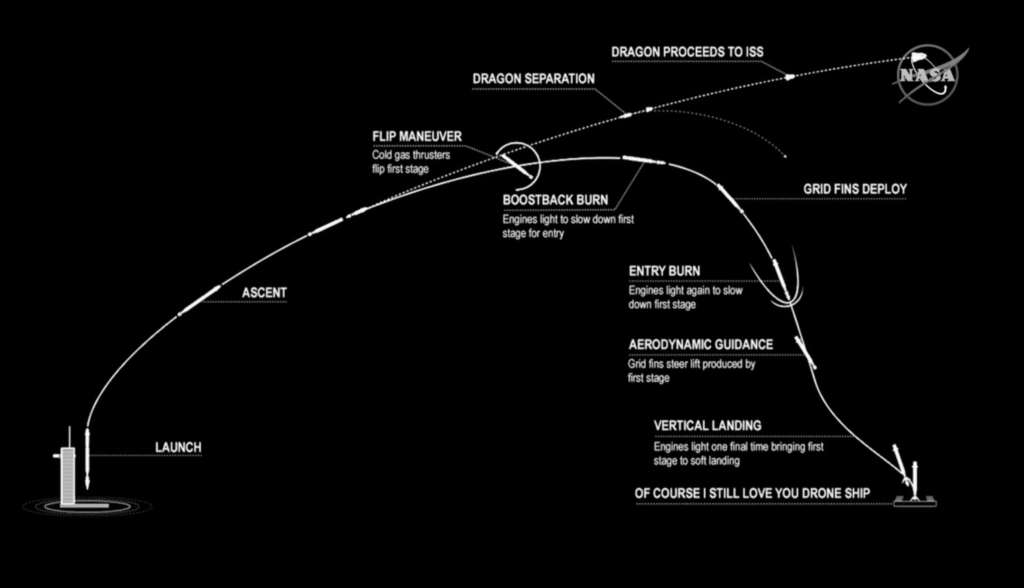
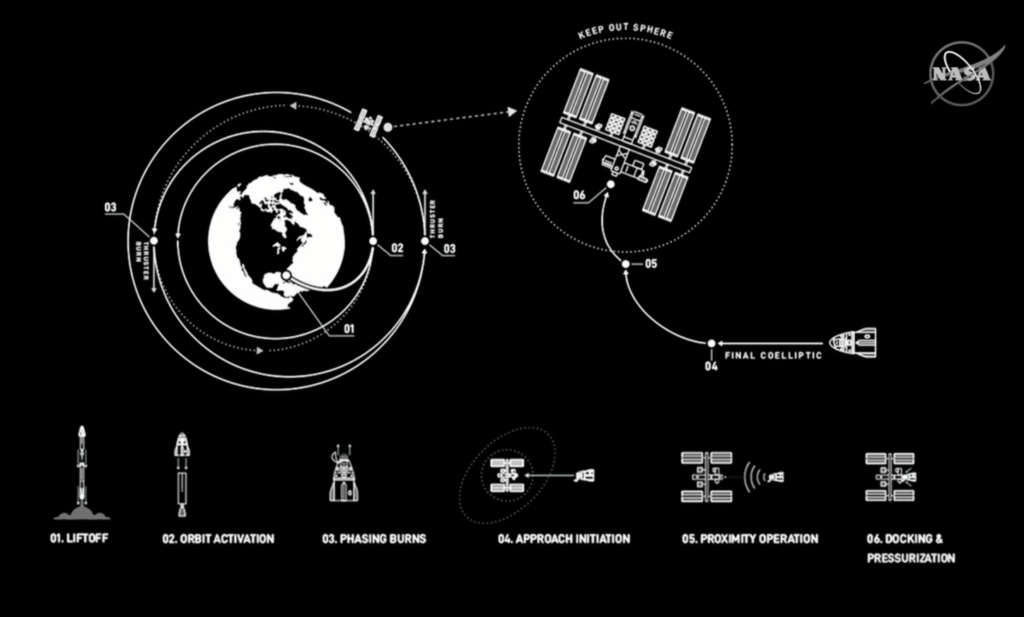
Les différentes phases du vol
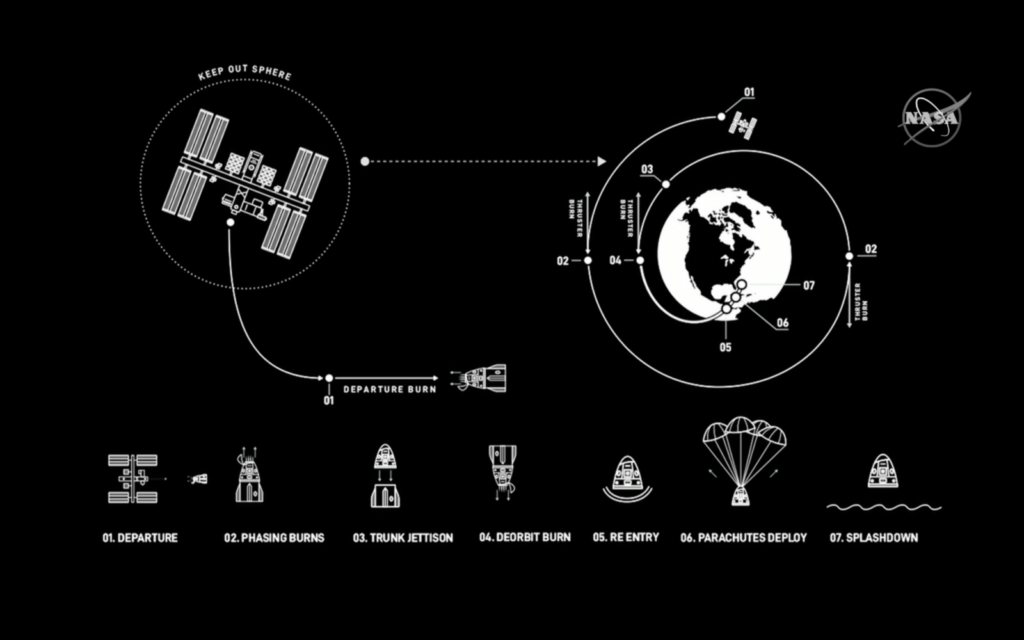
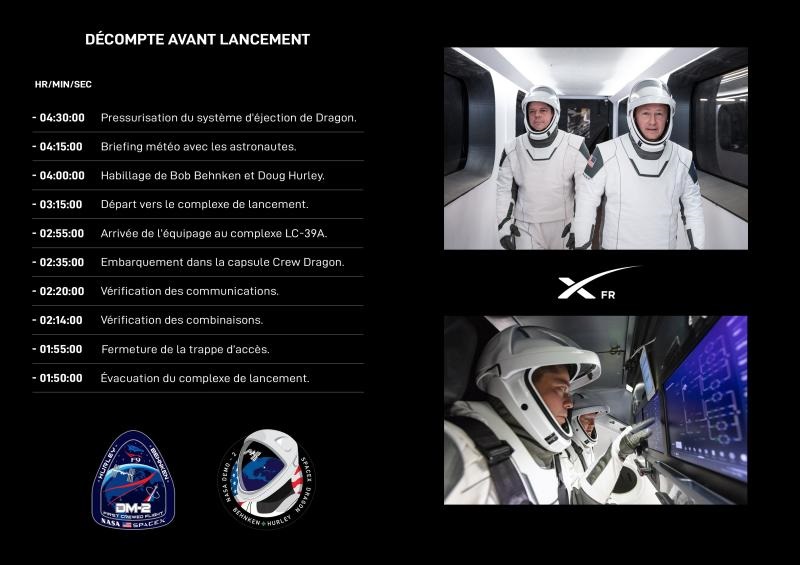
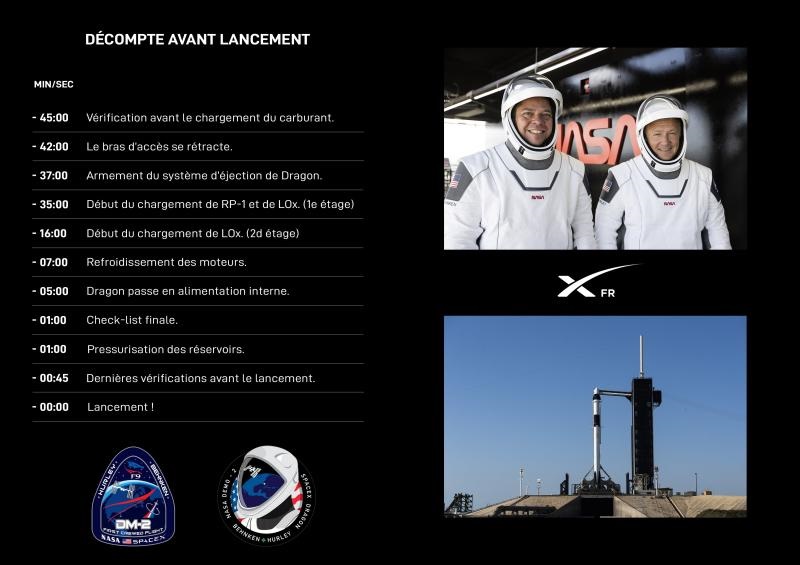
Le décompte avant lancement
Voici à quoi devrait ressembler la mission cruciale de SpaceX et de la NASA sur le Crew Dragon, le 27 mai
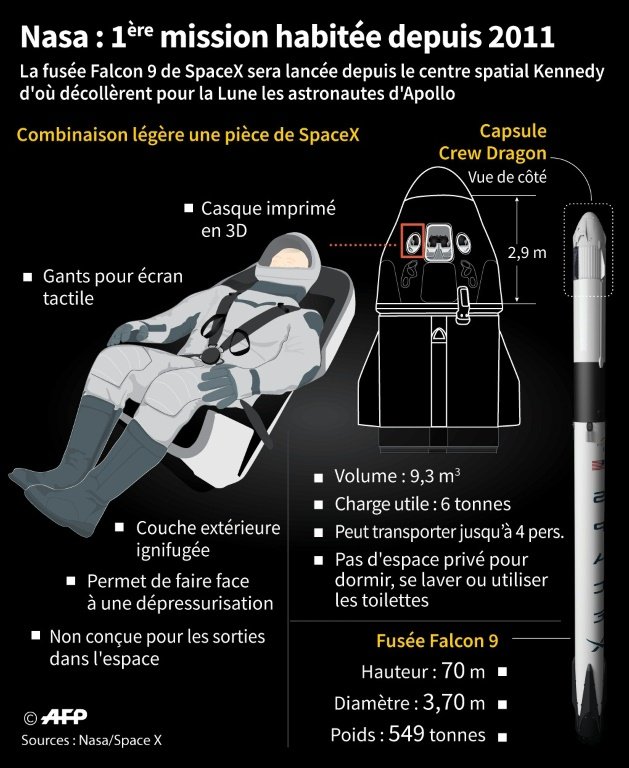
Infographie
Voici une petite infographie qui présente le vol
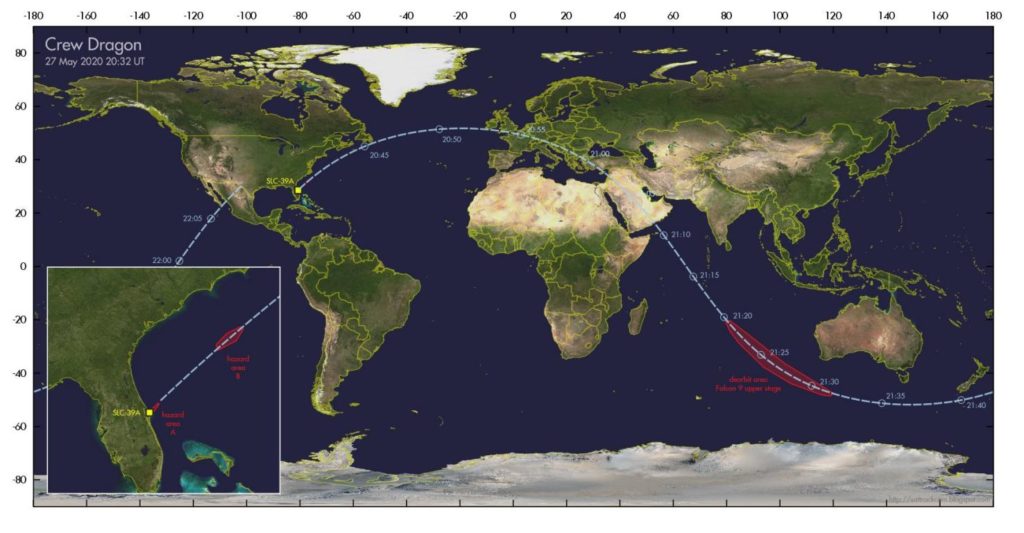
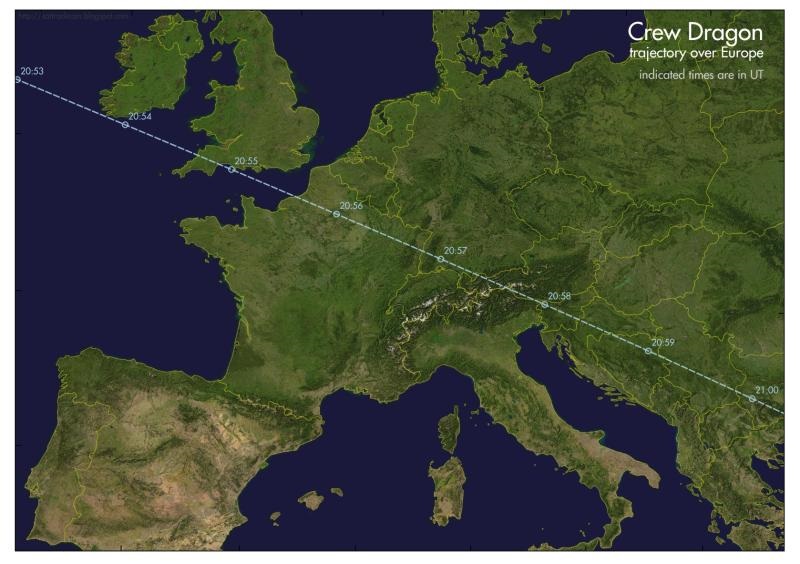
Le Crew Dragon sera très probablement visible à l’œil nu au dessus de la France, 20min après son décollage depuis la Floride (vers 22h55 ici)
Et si tout se passe bien, le vaisseau Crew Dragon pourrait même être visible au dessus du nord de la France. Les temps de passage indiqués sont en UT (pour CEST, ajouter 2 heures et pour la BST, ajouter 1 heure).
Timeline complète et détaillée du vol (en anglais)
COUNTDOWN AND LAUNCH TIMELINE
HR/MIN/SEC |
EVENT |
|---|---|
– 04:59:59 |
The Dragon Capsule aligns its inertial measurement units and is configured for launch |
– 04:30:00 |
The Crew Dragon hypergolic fuels for reaction control thrusters and the superdraco abort motors are pressurized for flight |
– 04:15:00 |
The Crew hears a weather briefing before they suit up |
– 04:05:00 |
The Crew is officially handed off from NASA to SpaceX, which is bit of a formality signifying the astronauts are officially in SpaceX’s hands |
– 04:00:00 |
The crew suits up at Kennedy Space Center’s Neil Armstrong Operations and Checkout Building |
– 03:22:00 |
The crew leaves the building and gets into the NASA and SpaceX’s Tesla Model X crew transportation vehicles. In other words, the crew gets suited up and ready to go in just 38 minutes, which is faster than most of us get ready for work in the morning |
– 03:15:00 |
The crew departs the Ops and checkout building and heads the 13.6 km (8.5 miles) to historic Launch Complex 39A |
– 02:55:00 |
The crew arrives at the pad. Since they will travel about 13.6 km in 20 minutes, it means they’ll only average around 40 km/h COME ON, they should turn on ludicrous mode and really put on a show! |
~ 02:40:00 |
The crew will do the ultimate walk across the Crew Access Arm, hopefully in slow mo so we get some awesome cinematic footage |
– 02:35:00 |
The crew enters the Dragon |
– 02:20:00 |
Communications check between the crew and the ground |
– 02:15:00 |
The seats rotate up putting the astronauts more on their backs and closer to the screens and controls |
– 02:14:00 |
They check for leaks in the suits and verify they’re good to go |
– 01:55:00 |
The hatch is closed up and the ground support crew leaves the pad |
– 01:10:00 |
The exact state and location of the International Space Station is uploaded to the Dragon Capsule |
– 00:45:00 |
The Go / No-Go Poll is taken to fuel up the vehicle |
– 00:42:00 |
The Crew Access Arm is retracted |
– 00:37:00 |
Dragon launch escape system is armed, which gives the crew the ability to abort from the rocket if there were a problem during fuel up or during ascent |
– 00:35:00 |
The RP-1 rocket fuel and the cryogenic liquid oxygen begin loading into the first stage of the rocket and RP-1 is loaded into the second stage |
– 00:35:00 |
1st stage LOX loading begins |
– 00:16:00 |
The Liquid oxygen begins filling the second stage |
– 00:07:00
|
Falcon 9 begins engine chill prior to launch |
– 00:05:00
|
Dragon transitions to internal power |
– 00:01:00
|
Command flight computer to begin final prelaunch checks |
– 00:01:00
|
Propellant tank pressurization to flight pressure begins |
– 00:00:45
|
SpaceX Launch Director verifies go for launch |
– 00:00:03
|
Engine controller commands engine ignition sequence to start |
– 00:00:00
|
Falcon 9 Liftoff |
LAUNCH, LANDING, AND DRAGON 2 DEPLOYMENT
HR/MIN/SEC |
EVENT |
|---|---|
00:00:58 |
Max Q (moment of peak mechanical stress on the rocket) |
00:02:30 |
1st stage main engine cutoff (MECO) |
00:02:34 |
1st and 2nd stages separate |
00:02:36 |
2nd stage engine starts |
00:07:12 |
1st stage entry burn |
00:08:43 |
2nd stage engine cutoff (SECO-1) |
00:08:45 |
1st stage begins its landing burn as it prepares to land on the autonomous spaceport drone ship |
00:09:09 |
1st stage landing |
00:12:00 |
Crew Dragon separates from 2nd stage |
00:12:46 |
Dragon nosecone open sequences begins |
00:49:06 |
After a few check outs of the draco reaction control thrusters and a few pointing maneuvers, there’s a phase burn of 16.11 m/s to align the orbits of the Dragon and the international space station |
09:44:44 |
There’s another phase adjustment burn |
11:10:15 |
The Dragon Capsule performs a 44.2 m/s burn using its draco thrusters to boost its orbit closer to the International Space Station |
11:55:01 |
There’s another burn, this time of 57.89 m/s which circularizes the orbit |
17:40:24 |
After a few mid course burns, the Crew Dragon is approaching the 400m keep out sphere and requires a Go / No-Go poll from Mission control to continue |
17:50:24 |
The Dragon Capsule enters the keep out sphere and hits Waypoint Zero which is 400m below the ISS |
18:15:24 |
The Dragon Capsule arrives at Waypoint 1 and holds approximately 220m away to align to the docking axis |
18:51:24 |
A final Go / No-Go Poll is given for docking |
18:56:24 |
The Dragon Capsule arrives at Waypoint 2 which is only 20m away and gets placed into a short hold |
19:01:24 |
The Dragon capsule departs Waypoint 2 and goes in for the docking |
19:06:24 |
the Dragon Capsule has contact and capture with the International Space Station |
19:06:25 |
A big sigh of relief from the crew and Mission Control, the Dragon is docked and the crew has officially arrived at the International Space Station! |