ethicallyHackingspace (eHs)® h4ck32n4u75™ (Hackernauts) Community Member
I'm very proud to have been choosen as ethicallyHackingspace(eHs)® h4ck32n4u75™ (Hackernauts) Community Member. Thank's to William Ferguson for this distinction.
The "h4ck32n4u75™" badge, pronounced "hackernauts,"...
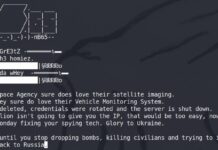
Hacktivism Goes Orbital: Investigating NB65’s Breach of ROSCOSMOS
In March of 2022, Network battalion 65 (NB65), a hacktivist affiliate of Anonymous, publicly asserted its successful breach of ROSCOSMOS’s satellite imaging capabilities in...
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
How I used MITRE EMB3D™ Threat Model to identify Siemens PLC vulnerabilities exploited by...
Introduction
In this article, I will show how I used the MITRE EMB3D™ Threat Model to identify vulnerabilities in SIEMENS PLCs that were exploited by...
The dark side of the DNS or the war of the port 53
I am very happy and proud that my article on DNS security has been accepted and published in the last issue of Hakin9 Magazine...
Very proud to receive the certificate of completion : « Introduction to Cybersecurity in...
I’m very proud to receive the following certificate of completion for having successfully completed the training course : « Introduction to Cybersecurity in Space...
The Interstellar Integrity (i2) magazine interviewed me about my passion for space and cybersecurity
I'm very proud to be featured in the second edition (nov 2023) of Interstellar Integrity (i2) released by ethicallyHackingspace(eHs)®.
Thank's to William Ferguson for this...
Very proud to have earned the Space Domain Cybersecurity digital badge from Teaching Science...
🚀 I’m proud to took part of the 3-day Space Domain Cybersecurity course provided by Teaching Science & Technology, Inc. (TSTI) in partnership with...
🌠🛰️ Space Cybersecurity Watch by CyberInflight, W23 – 2023
CyberInflight and Florent Rizzo released a new 🌠🛰️ Space Cybersecurity Weekly Watch 🛰️🌠 for Week 23 (May 30 - June 5, 2023). The team consolidates...
Reaching for the Stars with Zero Trust: Space Domain Applications
In this article, we will explore if we can apply Zero Trust in space domain, for example in satellites or space missions, how and...