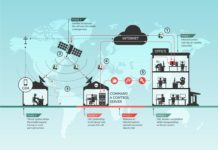
Back to Turla or how a Russian-speaking cyber-espionage group exploits satellites
Kaspersky Lab experts were the first to reveal in 2015 that the Russian hacker group Turla APT had exploited and hijacked satellite feeds to...
🌠🛰️ Space Cybersecurity Watch by CyberInflight, W23 – 2023
CyberInflight and Florent Rizzo released a new 🌠🛰️ Space Cybersecurity Weekly Watch 🛰️🌠 for Week 23 (May 30 - June 5, 2023). The team consolidates...
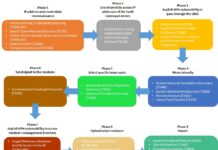
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
My cybersecurity review for 2024
What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I've had some incredible opportunities and I've...
ethicallyHackingspace (eHs)® h4ck32n4u75™ (Hackernauts) Community Member
I'm very proud to have been choosen as ethicallyHackingspace(eHs)® h4ck32n4u75™ (Hackernauts) Community Member. Thank's to William Ferguson for this distinction.
The "h4ck32n4u75™" badge, pronounced "hackernauts,"...
CYSAT’21, le 1er événement européen consacré à la cybersécurité de l’industrie spatiale
CYSEC, une entreprise suisse spécialisée dans la cybersécurité, co-organise avec AP-Swiss, la plateforme "Ambassadeurs" du programme d'applications de l'Agence Spatiale Européenne (ESA) en Suisse,...
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
“Introduction to Cybersecurity in Space Systems” with Tim Fowler is coming up during the...
Tim Fowler will provide a training course called "Introduction to Cybersecurity in Space Systems" at "The Most Offensive Con that Ever Offensived – Bypass...
Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Introduction
In this paper, I choose to investigate the Viasat cyber attack that occurred on 24 February, 2022. First, I will summarize the chronology of...
Exploring the power of the METEORSTORM™ framework — a framework built for full-spectrum modeling...
I'm very proud to have successfully taken up a new challenge exam in beta version about METEORSTORM™ framework which allowed me to obtain the...