What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I’ve had some incredible opportunities and I’ve been able to do some really interesting things.
I continue my role as ambassador for the Aerospace industry within the “L’Aéro Recrute” program with the support of My Job Glasses and GIFAS – Groupement des Industries Françaises Aéronautiques et Spatiales, to promote the Aerospace, Sace, Defense and Security sector.
I took part of the « Introduction to Cybersecurity in Space Systems » course provided by Tim Fowler during the march summit, The Most Offensive Con that Ever Offensived – Bypass Edition! organized by Antisyphon Training. More here.
My work about the analysis of the Viasat Cyber Attack has been quoted and highlighted by Tim Fowler and Angelina Tsuboi in there courses:
- Introduction to Cybersecurity in Space Systems with Tim Fowler
- Satellite Cybersecurity Foundations course by Angelina Tsuboi
- My article about the analysis of the Viasat cyber attack with the MITRE ATT&CK framework
- I also wrote a post mortem investigation about the Viasat Cyber Attack
- My LinkedIn group about Space Cybersecurity Community
I successfully passed the Certificate of Competence in Zero Trust (CCZT) from the Cloud Security Alliance (CSA). CCZT enables you to understand and implement Zero Trust principles into business planning, enterprise architectures, and technology deployments. More about CCZT.
I was quoted in the following article alongside Gerome Billois (Partner – Cybersecurity and Digital Trust – Wavestone) and Martial Gervaise (Cybersecurity Expert – Former Deputy Director at Orange Group). This article shows how important it’s to have a guideline in your cybersecurity career. This article shows also how it’s important to share whith others. It’s not by staying on your own that you grow the community. It’s by sharing that we collectively increase our skills. Cybersecurity grows when it’s shared.
I was elected as a CyberStar (or SpaceCyberStar) by Yohann BAUZIL. CyberStar is a program that highlights those who work to make cybersecurity a reality on a daily basis, either by sharing their knowledge or by their work.
I was choosen as ethicallyHackingspace(eHs)® h4ck32n4u75™ (Hackernauts) Community Member. Thank’s to William Ferguson for this distinction.
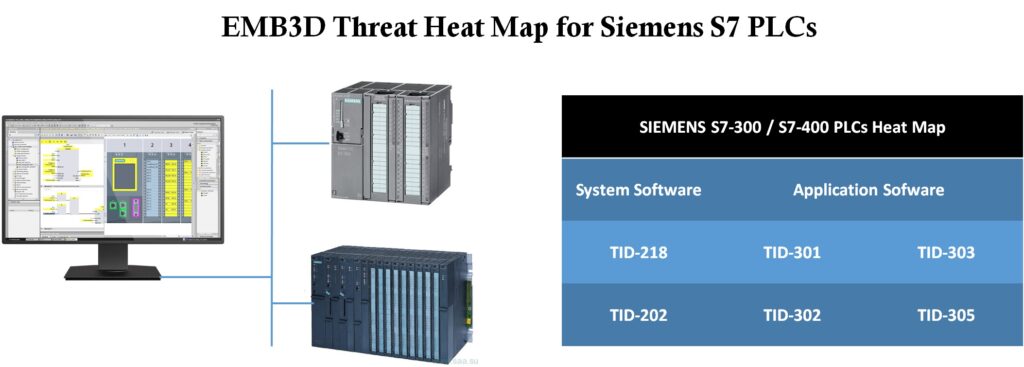
I wrote an article to explain how I used the new MITRE EMB3D™ threat model to identify Siemens PLC vulnerabilities potentially exploited by the Stuxnet worm. On May 13, 2024, MITRE released EMB3D™, a cybersecurity threat model for embedded devices. I carried out the following exercise to test and evaluate this new model.
- The first step was to identify the properties of the Siemens PLC by analyzing the data sheet.
- Next, I used the Properties tool to select the properties relevant to Siemens PLCs.
- Finally, I used the mapping tool to list the threats that represent a viable risk for Siemens PLCs.
- I checked to confirm that these vulnerabilities have been exploited by the Stuxnet worm.
- I used the Associated mitigations to propose a list of mitigations to the threats that pose a viable risk to the Siemens S7 series PLC.
- I finally mapped the associated mitigations with IEC 62443 4-2 framework
I successfully passed the CISM (Certified Information Security Manager) from ISACA. You can view my experience and tips after successfully passed this amazing certification here.
This journey has been both challenging and rewarding, filled with extensive study and deep dives into security governance, incident management, risk management and information security programs.
I’m proud to have achieved this important milestone in my career. I look forward to leveraging these skills and expertise to drive impactful security initiatives and contribute to the community.
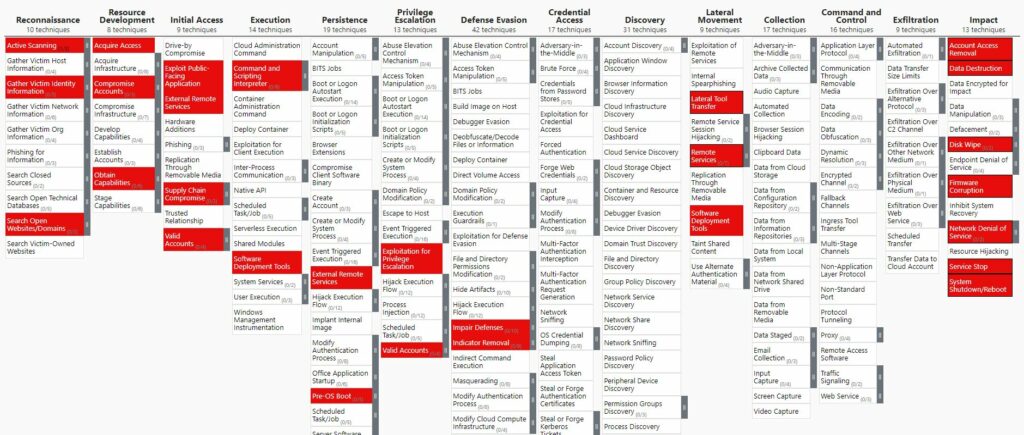
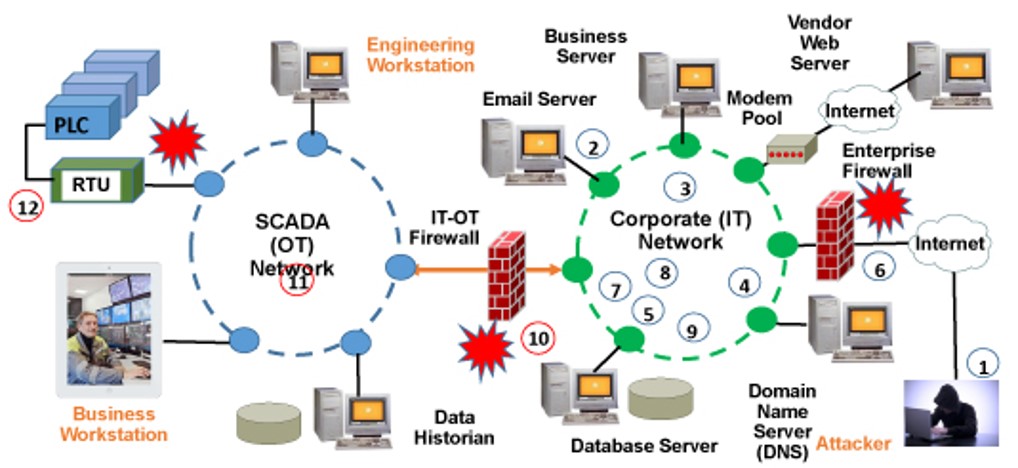
I wrote an article on how to model an attack on an Industrial Control Systems (ICS). In this article, I explain why attacks on OT (Operational Technology) systems are made easier due to the OT/IT convergence.
Then, I describe that attacks on OT and ICS systems are modeled by the ICS Cyber Kill Chain and the MITRE ATT&CK for ICS Matrix described below.
I am very happy and proud that my article on DNS security has been accepted and published in the last issue of Hakin9 Magazine after being reviewed by the editorial board.
This new issue of Hakin9 Magazine, titled « Dark Web Vol.3 », is an exploratory journey into the shadowy realms of the internet and the cybersecurity challenges that lurk within.
The title of my article is « The dark side of the DNS or the war of the port 53 ». To know more here.
=========
I’d like to thank everyone who has followed me, encouraged me and supported me.
I hope all the information I share with you is interesting and helps you keep up to date and learn more.
But stay tuned because 2025 promises to be just as incredible and intense.
Until then, take care.