Aerospace cybersecurity manuals bundle : satellites, drones, airplanes, and signals intelligence systems
Angelina Tsuboi is a programmer, mechatronics developer and Engineer, a pilot, a Scientific Researcher and cybersecurity researcher. She is currently working for NASA. She...
CYSAT’21, le 1er événement européen consacré à la cybersécurité de l’industrie spatiale
CYSEC, une entreprise suisse spécialisée dans la cybersécurité, co-organise avec AP-Swiss, la plateforme "Ambassadeurs" du programme d'applications de l'Agence Spatiale Européenne (ESA) en Suisse,...
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
SpaceSec, the Workshop on the Security of Space and Satellite Systems
SpaceSec is the Workshop on the Security of Space and Satellite Systems
https://spacesec.info/
SpaceSec 2023 took place on the 27 February 2023 in San Diego, California.
https://www.ndss-symposium.org/ndss-program/spacesec-2023/
The...
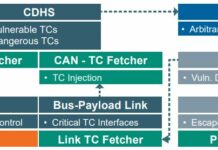
Space Odyssey: An Experimental Software Security Analysis of Satellites
The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper...
New upcoming course : “Aerospace Cybersecurity: Satellite Hacking” made by Angelina Tsuboi in collaboration...
We are very excited to announce a new upcoming course, "Aerospace Cybersecurity: Satellite Hacking" led by Angelina Tsuboi in collaboration with PenTestMag.
This comprehensive course...
Live Webinar on Aerospace Cybersecurity: Satellite Hacking
Find below the first ever webinar by PenTest Mag! Hosted by Timothy Hoffman, the talk will evolve around the topic of the online course...
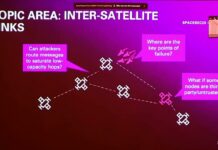
CYSAT ’23, a space cybersecurity conference : Full Keynotes and Presentations
CYSAT ’23 is the first conference in Europe dedicated to satellite and space industry cyber security. It took place from 26 to 27 April...
Indiana University – Kelley School of Business launches a new academic program dedicated to...
Russia’s cyberattack on ViaSat on the eve of its invasion of Ukraine put the cyber fragility of space systems high on the agenda and...
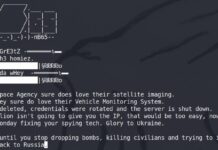
Hacktivism Goes Orbital: Investigating NB65’s Breach of ROSCOSMOS
In March of 2022, Network battalion 65 (NB65), a hacktivist affiliate of Anonymous, publicly asserted its successful breach of ROSCOSMOS’s satellite imaging capabilities in...