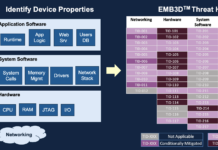
MITRE Releases EMB3D™ – A Cybersecurity Threat Model for Embedded Devices
Collaborative framework provides common understanding to mitigate cyber threats to critical infrastructure
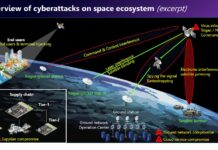
MCLEAN, Va. & BEDFORD, Mass., May 13, 2024--(BUSINESS WIRE)--The EMB3D Threat Model is...
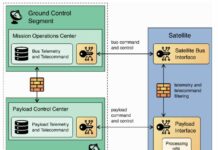
NIST released IR 8401, a new Cybersecurity Framework applied to the ground segment of...
NIST released IR 8401, a new guidance named “Satellite Ground Segment: Applying the Cybersecurity Framework to Assure Satellite Command and Control”.
NIST IR 8401 is...
First manned SpaceX Crew Dragon flight set for May 27 liftoff
Barring a last-minute postponement, a SpaceX Crew Dragon capsule will take off from the top of a Falcon 9 rocket on May 27th. The...
[Book] The Battle Beyond: Fighting and Winning the Coming War in Space
Fundamentally, Paul Szymanski and Jerry Drew remind us that--more than just simply a clash of weapons--all warfare manifests as a competition between human minds....
Airbus Defence and Space a été sélectionné pour construire l’orbiteur qui ramènera vers la...
L'annonce a été faite ce mercredi 29 juillet 2020 par Dirk Hoke, le Chief Executive Officer (CEO) d'Airbus Defence and Space (ADS).
Airbus Defence and...
Coverage by CyberInflight of the Russian satellite telecom Dozor-Teleport Attack
CyberInflight (www.cyberinflight.com) is an independant consulting and business intelligence company dedicated to the topic of Aerospace Cybersecurity. CyberInflight’s goal is to raise the global cybersecurity...
Back to the lastest “In-Flight Abort Test” from SpaceX before the first manned flight...
On Sunday, January 19, 2020, the last big test for SpaceX, Elon Musk's company, took place successfully. It was to simulate a failure of...
DEF CON 29 Aerospace Village Videos
DEF CON Aerospace Village is a researcher led, non-profit whose mission is to build a diverse community focussed on the security of everything from...
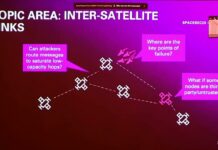
SpaceSec, the Workshop on the Security of Space and Satellite Systems
SpaceSec is the Workshop on the Security of Space and Satellite Systems
https://spacesec.info/
SpaceSec 2023 took place on the 27 February 2023 in San Diego, California.
https://www.ndss-symposium.org/ndss-program/spacesec-2023/
The...
Thales demo at CYSAT: what was the point again
CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading...


![[Book] The Battle Beyond: Fighting and Winning the Coming War in Space](https://www.spacesecurity.info/wp-content/uploads/2023/12/The-Battle-Beyond-Fighting-and-Winning-the-Coming-War-in-Space-218x150.jpg)