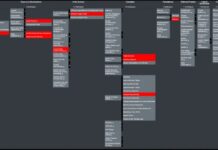
Top 25 most dangerous software weaknesses than can affect satellites in 2023
Issues of vulnerabilities of space systems to cyber attacks has long been ignored for reasons common to industrial systems or SCADA (Supervisory Control And...
Sample of the last Space Cybersecurity Market Intelligence 2023 Report from CyberInflight
CyberInflight and Florent Rizzo shared an excerpt of their last Space Cybersecurity Market Intelligence 2023 Report.
Here is what Florent said in French about this...
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
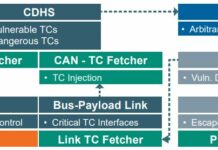
An analysis of the Thales satellite hacking demo CYSAT 2023 by SPARTA team
Brandon Bailey & Brad Roeher from the SPARTA team analyzed, in this article, Thales Group’s CYSAT ’23 presentation material to deconstruct the experiment, extract lessons...
Space Odyssey: An Experimental Software Security Analysis of Satellites
The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper...
Hacking demo at CYSAT 2023: world first or “déjà vu”❓ Here is what I know 👇
CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading...
Thales demo at CYSAT: what was the point again
CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading...
Thales prepares to secure European infrastructures against attacks from future quantum computers
14 April 2023, Paris, La Défense (Press Release)
As a driving force in the second quantum revolution, Thales has joined forces with around twenty deep...
Thales veut développer l’Internet quantique via satellite
Marko Erman, le directeur scientifique de Thales, est intervenu dans l'émission Tech&Co de BFM Business, sur le thème de l'Internet quantique via satellite.
Dans cet...
Thales seizes control of ESA demonstration satellite in first cybersecurity exercise of its kind
25 April 2023, Paris,
For the third edition of CYSAT, the European event entirely dedicated to cybersecurity for the space industry, taking place on...