Issues of vulnerabilities of space systems to cyber attacks has long been ignored for reasons common to industrial systems or SCADA (Supervisory Control And Data Acquisition) type.
Reality and experience show that today’s world is not the same as the old world. It’s now essential to consider the vulnerability of space systems to cyber attacks.
The latest generation of satellites, such as those from SpaceX, are looking to keep costs down, so most of them use Open Source software. This makes them just as vulnerable to cyber threats as any other piece of hardware.
In the age of globalisation, the supply chain is often internationalised. It’s difficult to control completely. The introduction of malicious components or software is not completely impossible for a motivated bad or adversary actor. For example, a backdoor could be introduced into the satellite’s components or software.
The ground stations with which satellites communicate are not all that isolated. The same applies to the command and control centres that pilot the satellites via the ground stations. Most of them need to communicate with the outside world, as they do with data centres, even if this is done via secure Internet links.
Access to the satellites may be physically impossible, but it’s still possible to gain access via their ground station or their command and control system. This is a potential gateway for a malicious actor.
Software is an inherent part of satellites, launchers and space systems. This is known as “on-board satellite software” or “software-defined satellite”.
Commercial players with an interest in cutting costs tend to ignore the cybersecurity of space systems by using Open Source software, reusing software code from other programmes, or even reusing old code.
Technically, the only way to avoid service interruptions is to ensure the technological redundancy of ground stations, electrical networks and hardware and software on board satellites. But poorly coded software, even if redundant, remains vulnerable.
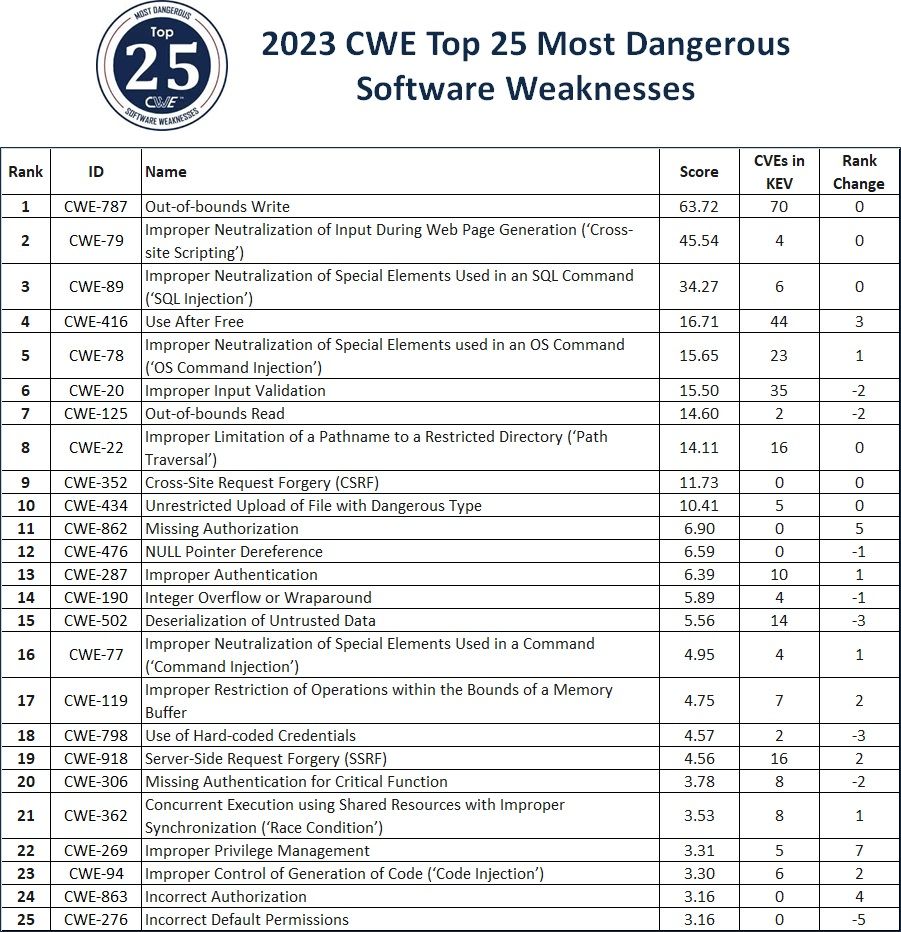
With this in mind, we’ve decided to take an increasing interest in software. We take this opportunity to remind you that the MITRE has just released the Top 25 most dangerous software weaknesses for 2023.
The list is based on an analysis of public vulnerability data in the National Institute of Standards and Technology (NIST)’s National Vulnerability Data (NVD) for root cause mappings to CWE (Common Weaknesses Enumeration) for years 2021 and 2022.
A total of 43,996 CVE from the Known Exploited Vulnerabilities (KEV) database were examined and a score was attached to each of them based on prevalence and severity.
A the top, you have : Out-of-bounds Write, Cross-site Scripting, SQL Injection, Use After Free, OS Command Injection, Improper Input Validation, Out-of-bounds Read, Path Traversal, Cross-Site Request Forgery (CSRF), and Unrestricted Upload of File with Dangerous Type.
More info here : https://cwe.mitre.org/top25/