Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Introduction
In this paper, I choose to investigate the Viasat cyber attack that occurred on 24 February, 2022. First, I will summarize the chronology of...
[Book] The Battle Beyond: Fighting and Winning the Coming War in Space
Fundamentally, Paul Szymanski and Jerry Drew remind us that--more than just simply a clash of weapons--all warfare manifests as a competition between human minds....
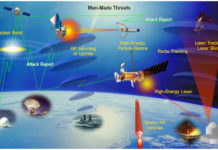
What are the threats to space systems?
In this article, we will try to identify the various threats to space systems.
This article is a synthesis of the CSIS (Center for Strategic...
My cybersecurity review for 2023
What an incredible end to 2023. I've had some wonderful experiences. I've successfully met many challenges in cybersecurity.
I took part of the 3-day...
Hack-A-Sat avec NoLimitSecu (podcast)
Le dernier numéro de NoLimitSecu revient sur la compétition "Hack-a-Sat", un programme de bug bounty de l’armée de l’air américaine (US Air Force) sous...
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the MITRE...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
Solarium CSC 2.0 has endorsed designation of space systems as a critical infrastructure sector
The Cyberspace Solarium Commission (CSC) was established in the John S. McCain National Defense Authorization Act for Fiscal Year 2019 to "develop a consensus...
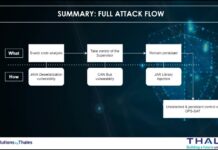
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
An analysis of the Viasat cyber attack with the MITRE ATT&CK® framework
Disclaimer
To do this analysis of the Viasat cyber attack, I used the open-source intelligence (1) of the team composed by Nicolò Boschetti (Cornell University),...
Fin du suspense : c’est avec le Crew Dragon de SpaceX que Thomas Pesquet...
Fin du suspense : c'est avec le Crew Dragon de SpaceX que Thomas Pesquet décollera l'année prochaine ! L'astronaute de l'ESA, l'Agence spatiale européenne,...

![[Book] The Battle Beyond: Fighting and Winning the Coming War in Space](https://www.spacesecurity.info/wp-content/uploads/2023/12/The-Battle-Beyond-Fighting-and-Winning-the-Coming-War-in-Space-218x150.jpg)