Aerospace cybersecurity manuals bundle : satellites, drones, airplanes, and signals intelligence systems
Angelina Tsuboi is a programmer, mechatronics developer and Engineer, a pilot, a Scientific Researcher and cybersecurity researcher. She is currently working for NASA. She...
« Aerospace Cybersecurity: Satellite Hacking » course review
I just successfully completed the comprehensive course on « Aerospace Cybersecurity: Satellite Hacking » and passed successfully the final exam with a result of...
ethicallyHackingspace (eHs)® h4ck32n4u75™ (Hackernauts) Community Member
I'm very proud to have been choosen as ethicallyHackingspace(eHs)® h4ck32n4u75™ (Hackernauts) Community Member. Thank's to William Ferguson for this distinction.
The "h4ck32n4u75™" badge, pronounced "hackernauts,"...
My cybersecurity review for 2023
What an incredible end to 2023. I've had some wonderful experiences. I've successfully met many challenges in cybersecurity.
I took part of the 3-day...
23 Tips to Pass CCSK (Certificate of Cloud Security Knowledge) from CSA at the...
At the beginning of April 2020, I successfully passed the CCSK certification (Certificate of Cloud Security Knowledge). Now, I give you some tips and...
Reaching for the Stars with Zero Trust: Space Domain Applications
In this article, we will explore if we can apply Zero Trust in space domain, for example in satellites or space missions, how and...
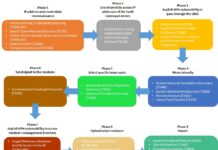
Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Introduction
In this paper, I choose to investigate the Viasat cyber attack that occurred on 24 February, 2022. First, I will summarize the chronology of...
Detecting Aircraft Spoofing With Fly-Catcher
Aviation technology is vulnerable to a wide range of cyber threats. Hackers can easily spoof "ghost" aircraft into the sky.
In order to tackle this...
The Interstellar Integrity (i2) magazine interviewed me about my passion for space and cybersecurity
I'm very proud to be featured in the second edition (nov 2023) of Interstellar Integrity (i2) released by ethicallyHackingspace(eHs)®.
Thank's to William Ferguson for this...
My work about the Viasat attack analysis featured in the SIGN.MEDIA #2 newsletter
I’m very proud to be featured by Olga Nasibullina and Tatiana Skydan in THE SIGN.MEDIA #2 newsletter.
Olga Nasibullina works mainly on cybersecurity workforce development,...