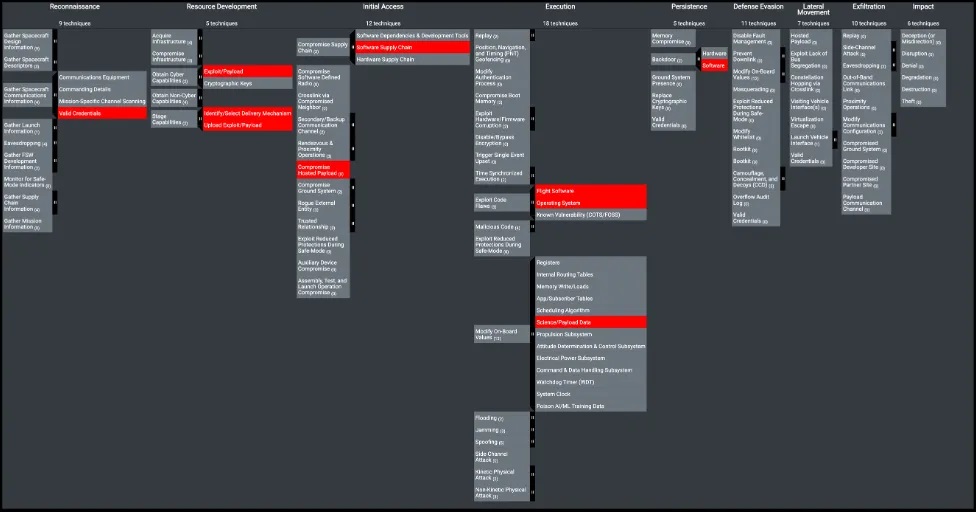
🔥 On Tuesday 25 April 2023, the MITRE Corporation released ATT&CK v13, the new version of its framework.
This new version includes significant updates and affects all matrices: Enterprise, Mobile and ICS.
In this article, we summarize the biggest changes : and will go through more details.
✔️ Addition of « Pseudocode analytics for Detection »: I understand this is the most important change in ATT&CK v13. It adds detailed recommendations to the TTPs in the Enterprise matrix to improve their detection by providing more precision and context on what to look for and collect. This new information can be consulted in the CAR (Cyber Analytics Repository) database.
✔️ Addition of new data sources for the Mobile matrix: Data sources represent information that can be collected from logs or probes. They also include characteristics that make it possible to identify the specific properties/values of a data source that are relevant to the detection of a technique or sub-technique.
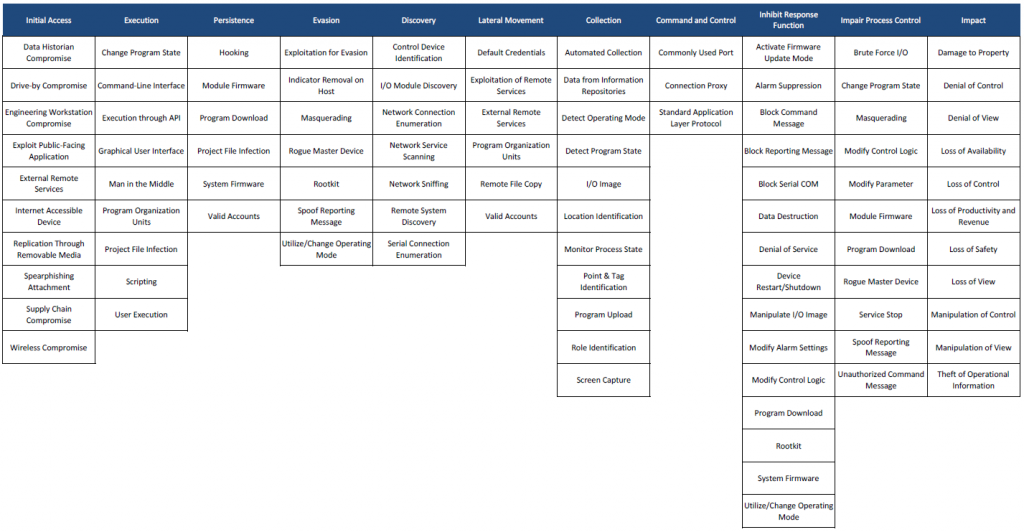
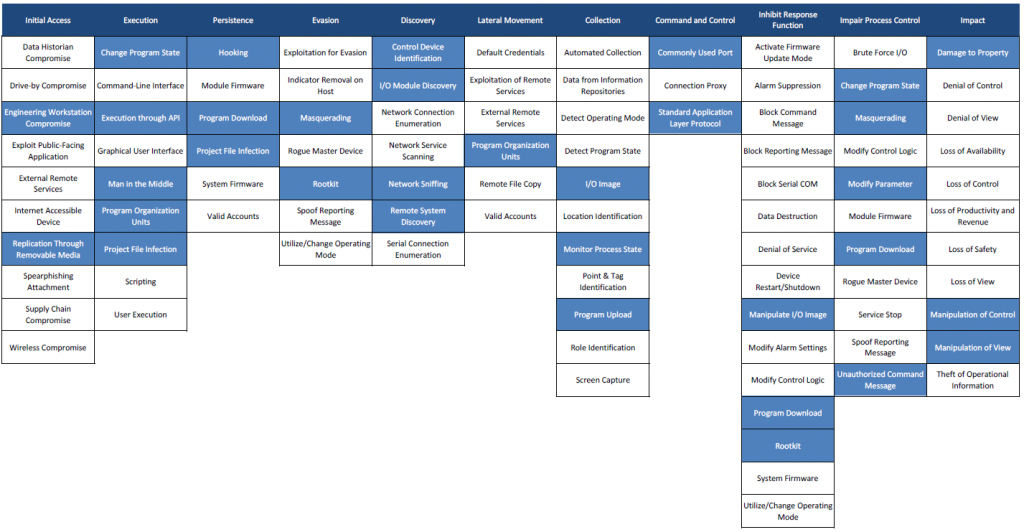
✔️ Update of the ICS matrix: overhaul of assets, addition of new techniques and refresh of campaign mapping
✔️ Update of APT groups and attack campaigns with the possibility of cross-domain mapping
✔️ Improved coverage of the Cloud: addition of new technologies and completion of execution and lateral movement techniques
✔️ Improved coverage of Linux: updated techniques and sub-techniques with a better understanding of attacks
✔️ Improvements to the web interface, mainly in the search module
✔️ New changelog types to help identify more precisely what has changed in ATT&CK.
“we’re working toward enhanced tools for lower-resourced defenders, improving ATT&CK’s website usability, enhancing ICS and Mobile parity with Enterprise, and evolving overall content and structure this year”
Amy L. Robertson
🤩 A v14 is already announced for October with more details at ATT&CKCon 4.0 which takes place on 24-25 October 2023 :
- upgraded coverage across domains
- renovated mitigations
- new cross-domain mappings
- more pseudocodes
- mobile structured detections
👉 More details in this article on the MITRE blog
More about MITRE ATT&CK framework
The MITRE ATT&CK framework is a globally recognized knowledge base and methodology for understanding, organizing, and classifying cyber threats and tactics used by adversaries during different stages of a cyber attack. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
The framework was developed by MITRE, a not-for-profit organization that operates federally funded research and development centers (FFRDCs) to address various challenges faced by the U.S. government. However, the framework has gained widespread adoption in the cybersecurity community and is used by organizations around the world.
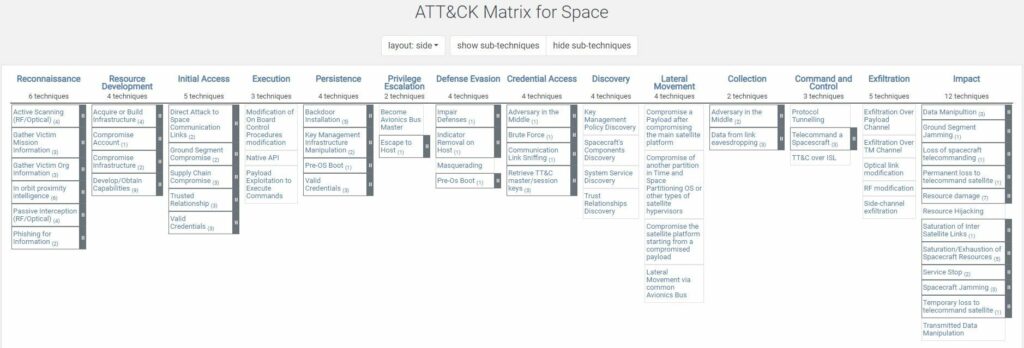
The MITRE ATT&CK framework provides a comprehensive model that describes the entire lifecycle of a cyber attack, from initial reconnaissance and weaponization to lateral movement, data exfiltration, and impact. It consists of a matrix that outlines various tactics and techniques employed by adversaries, along with information on the platforms they target (e.g., Windows, macOS, Linux) and the types of software they use.
The framework is organized into several categories, including Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Exfiltration, and Impact. Each category is further divided into specific techniques and sub-techniques that adversaries may employ.
For each technique, the framework provides detailed information on how it works, the potential impact, and real-world examples of its usage by known threat actors. This knowledge base allows organizations to better understand the tactics and techniques employed by adversaries and assists in building effective defensive strategies and improving incident response capabilities.
By utilizing the MITRE ATT&CK framework, organizations can map observed adversary behaviors to specific techniques, identify security gaps, prioritize defenses, develop threat intelligence, and share information with the broader cybersecurity community. The framework serves as a common language and reference point for cybersecurity professionals, enabling them to collaborate and exchange knowledge on emerging threats and effective defense strategies.
Overall, the MITRE ATT&CK framework plays a crucial role in enhancing cybersecurity awareness and readiness, facilitating the development of proactive defense measures, and improving the overall resilience of organizations against cyber attacks.
Go to the MITRE ATT&CK framework here.